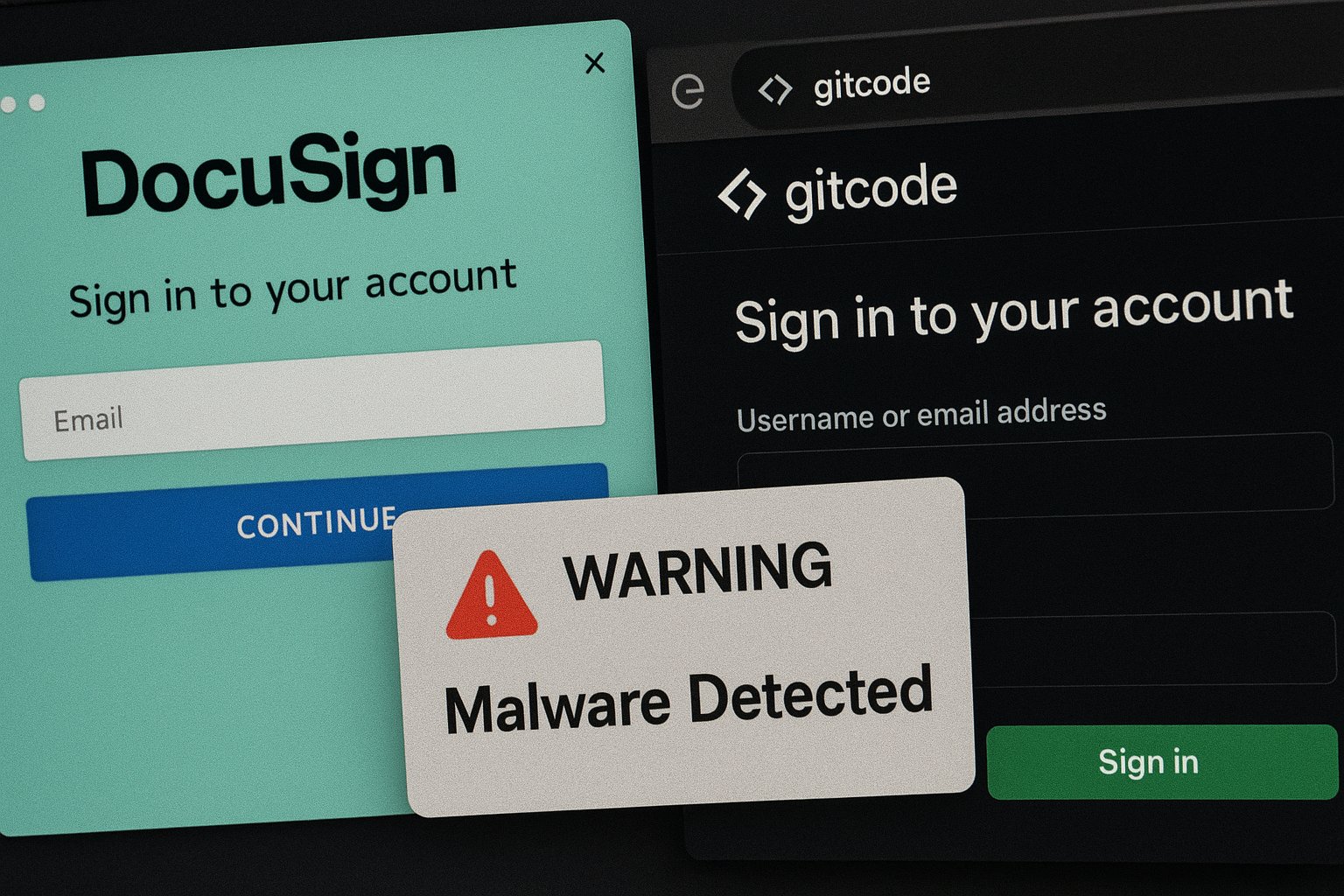
Cyber threat hunters have raised alarms over a new campaign deploying counterfeit websites to trick users into executing harmful PowerShell scripts, leading to infections by the NetSupport RAT malware. The DomainTools Investigations (DTI) team revealed in a comprehensive report that these deceptive sites masquerade as reputable platforms such as Gitcode and DocuSign.
The DTI team reported that the malicious multi-stage downloader PowerShell scripts were first observed on websites designed to look legitimate, aiming to entice users into copying and executing scripts from their Windows Run command. In executing these commands, unsuspecting users inadvertently initiate a chain of downloads that facilite the deployment of the NetSupport RAT, an established remote access Trojan known for its malicious intent.
These counterfeit sites appear to be proliferated through social engineering tactics, notably via email and social media. The malicious PowerShell scripts located on these fake Gitcode sites execute a series of intermediate scripts from a compromised external server, resulting in the installation of the NetSupport RAT on victim computers.
One shocking tactic employed by these sites includes the use of ClickFix-style CAPTCHA verifications, which create an illusion of legitimacy while persuading users to execute the harmful script. Completing the CAPTCHA triggers clipboard poisoning, covertly copying an obfuscated command to the user’s clipboard without their knowledge.
Victims, under the guise of a legitimate operation, are guided to open the Windows Run dialog and paste the command, executing a script that downloads a persistence mechanism, referred to as wbdims.exe, from GitHub. This mechanism ensures that malicious code is launched automatically upon user login, significantly increasing the risk of compromise. As of the time of investigation, the payload was no longer available; however, it was expected to trigger further malicious actions on the user’s machine.
DomainTools believes that the multiple stages involved in the attack serve to evade detection, offering a more resilient approach to overcoming security measures that could potentially mitigate these malicious operations. Notably, tools like NetSupport Manager are often exploited by various cybercriminal groups, including FIN7 and Scarlet Goldfinch, indicating a concerning trend in the misuse of legitimate software for malicious purposes.
As investigations continue, it remains unclear who orchestrates this campaign; however, the strategies employed mirror tactics previously utilized in the SocGholish operations discovered in late 2024. As users become more aware of such malicious tactics, organizations within the cybersecurity domain are urged to reinforce their defenses against the proliferation of these deceptive websites.