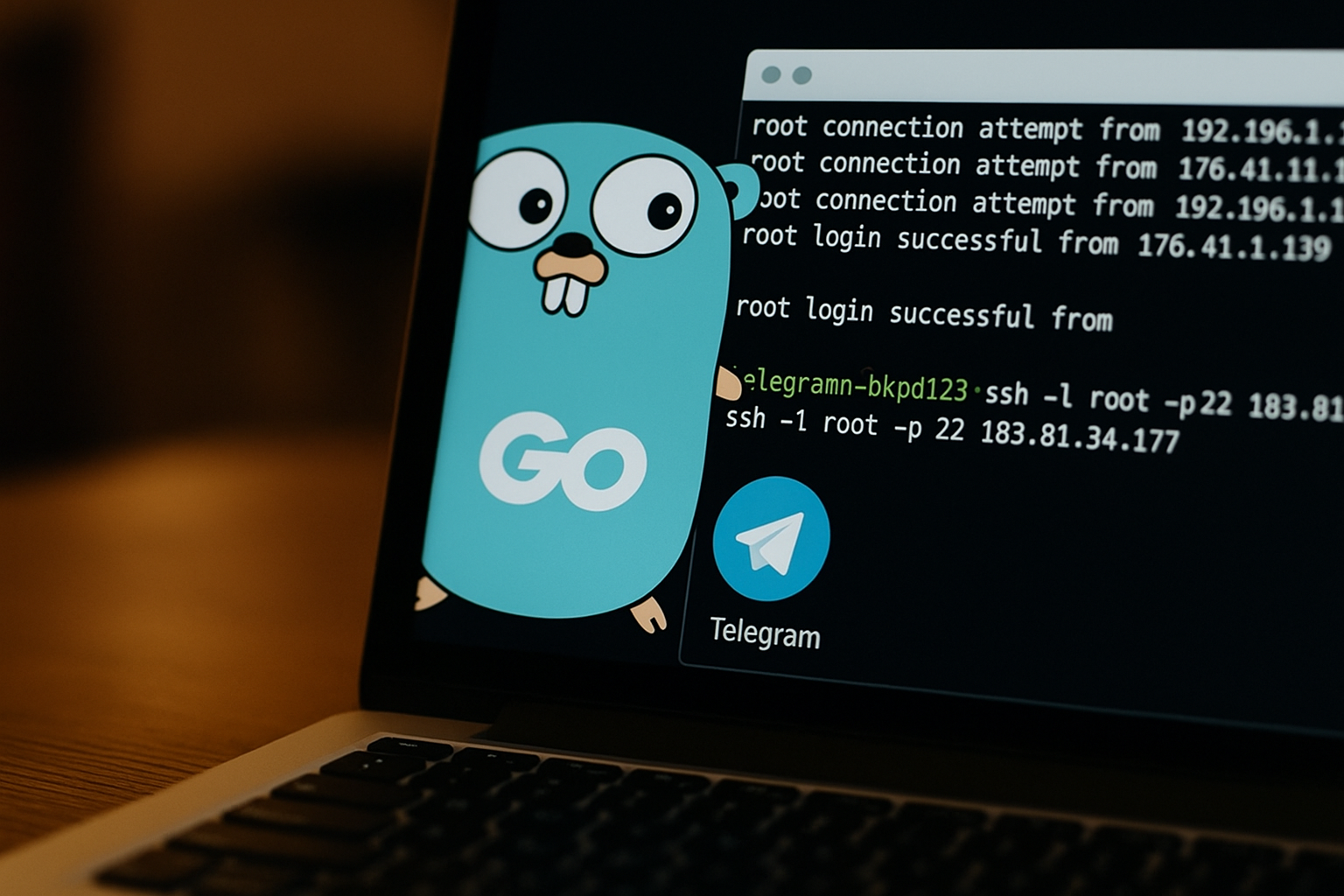
Security researchers have uncovered a malicious Go module that masquerades as an SSH brute-forcing tool but secretly exfiltrates credentials to a threat actor via Telegram. The package, named golang-random-ip-ssh-bruteforce, was linked to a GitHub account once operated by the user IllDieAnyway (G3TT). According to Kirill Boychenko of Socket, the malware operates while quietly sending the harvested data to a Telegram bot controlled by the attacker. The details were described in a post on Socket’s blog.
The Go module was published on June 24, 2022, and has since been associated with IllDieAnyway. It remains accessible on its pkg.go.dev page, which documents the package and its operational approach. The same lineage points to a GitHub identity that is no longer active but has left a footprint in the module ecosystem.
Operatively, the malware scans random IPv4 addresses for exposed SSH services on TCP port 22 and then attempts to brute-force login using an embedded username-password list. In addition to credential attempts, the module exfiltrates any successful credentials to the attacker via a Telegram bot.
A notable technical detail is that the malware deliberately disables host key verification by setting InsecureIgnoreHostKey as its HostKeyCallback, allowing the SSH client to accept connections from any server regardless of identity. This makes it easier for the malware to progress without standard SSH verification checks.
The embedded wordlist is sparse, featuring two usernames – root and admin – paired with commonly weak passwords such as root, test, password, admin, 12345678, 1234, qwerty, webadmin, webmaster, techsupport, letmein, and Passw@rd.
The code runs in an infinite loop to generate IPv4 addresses and launch concurrent SSH login attempts across the wordlist. If a login succeeds, the credentials are sent to a threat actor–controlled Telegram bot named @sshZXC_bot (ssh_bot) via the Telegram Bot API, with acknowledgments then forwarded to an account tracked as @io_ping (Gett).
Further context about the actor and their tooling is provided by an Internet Archive snapshot of IllDieAnyway’s now-removed GitHub portfolio, which previously included an IP port scanner and even a PHP-based command-and-control (C2) botnet called Selica-C2.
The actor’s broader footprint includes a YouTube channel that hosts content about hacking a Telegram bot and other related topics, suggesting a pattern of activity that aligns with reported Russian-origin cyber threats.
Security researchers emphasize that the package offloads scanning and password guessing to unwitting operators, disperses risk across multiple IPs, and funnels successful credentials to a single actor-controlled Telegram endpoint. Experts warn this underscores the ongoing risk in software supply chains and the importance of verifying SSH hosts and minimizing exposure to brute-force attempts. For ongoing coverage and analysis, readers can follow related updates via external security news sources and channels linked below.