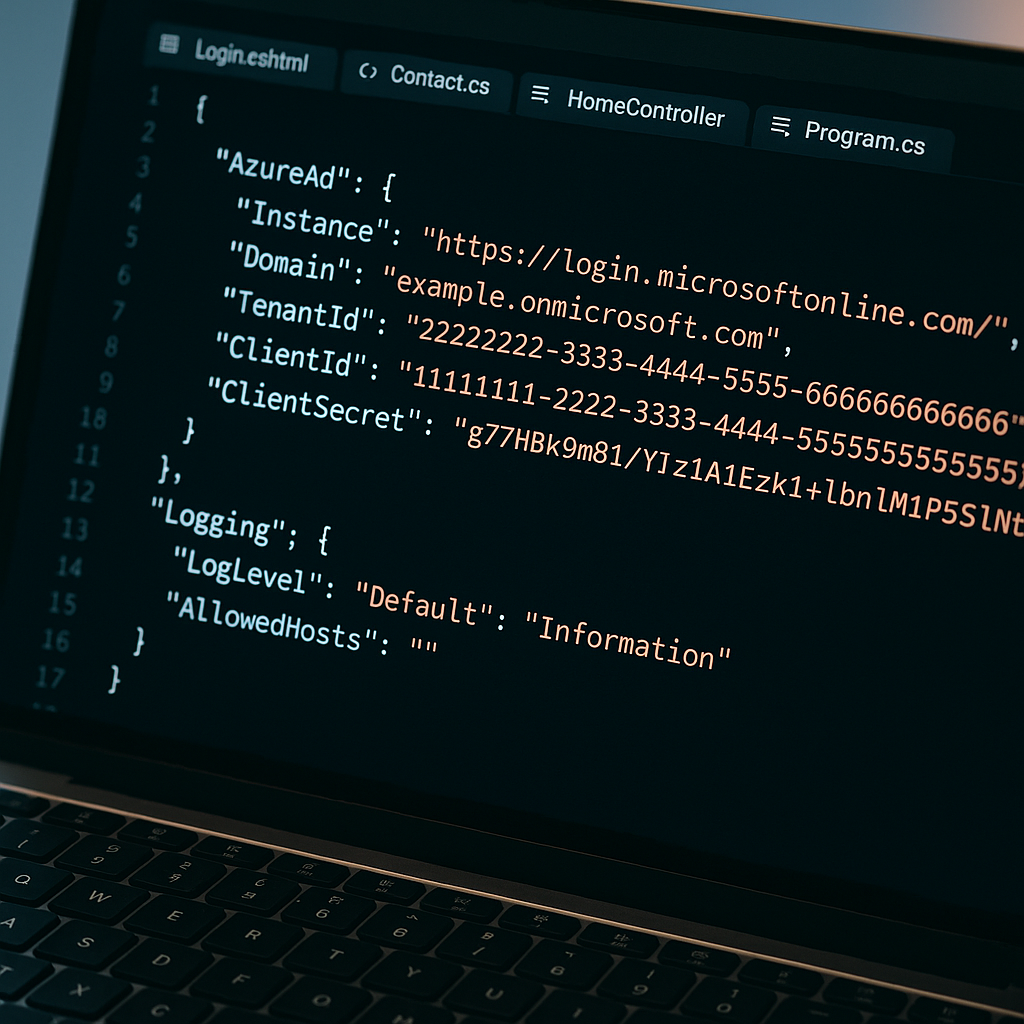
A publicly accessible configuration file used by ASP.NET Core applications has been found leaking credentials for Azure Active Directory, potentially enabling attackers to authenticate via Microsoft’s OAuth 2.0 endpoints and infiltrate Azure cloud environments. Researchers from Resecurity’s HUNTER team disclosed that Azure AD credentials – specifically ClientId and ClientSecret – were exposed in an Application Settings file (appsettings.json) accessible on the public Internet, a disclosure published in a blog post.
The researchers warn that the leak is a high-severity exposure because it could allow a threat actor to authenticate as the trusted application. “The critical risk lies in the fact that this file was publicly accessible over the Internet,” the post notes, meaning anyone – from opportunistic bots to advanced attackers – could harvest the credentials and use them to compromise cloud accounts.
With the credentials in hand, an attacker could use the leaked ClientId and ClientSecret to obtain an access token via the OAuth2 Client Credentials flow and then call the Microsoft Graph API to enumerate users, groups and directory roles within the tenant. The blog also describes how an attacker could identify which applications have been granted permissions and what scopes they hold, enabling further intrusion. The researchers emphasize that high-value groups, such as global administrators, are especially attractive targets because compromising one member can grant broad tenant control.
Beyond immediate access, the leak underscores a broader chronic issue: the exposure of secrets and poor secrets management in cloud-native applications. The post quotes, “What appears to be a harmless JSON configuration file can in reality act as a master key to an organization’s cloud kingdom,” highlighting how appsettings.json often stores credentials and tokens for cloud services that, if exposed, can unlock Azure AD identities, Graph data, storage accounts and privileged administrator functions.
Experts urge organizations to curb this risk through regular scanning, code reviews and secure secret management practices. Recommended steps include restricting file access, removing secrets from code and configuration files, rotating exposed credentials immediately, enforcing the principle of least privilege, and deploying vaults such as Azure Key Vault or AWS Secrets Manager, along with monitoring and alerting on credential use.
Cloud environments remain particularly vulnerable to such misconfigurations due to misconfigured Internet-facing servers, deployment practices, and the temptation to hardcode sensitive values in configuration files. The researchers’ findings serve as a cautionary tale for developers and security teams alike to treat appsettings.json as potentially dangerous if not properly secured.