The campaign was uncovered by Acronis’ Threat Research Unit, which said FileFix appeared in the wild in late August and represents the first in-the-wild instance that does not strictly adhere to the original Proof-of-Concept model demonstrated by a researcher known as mr.d0x. Acronis noted a spike in VirusTotal submissions and phishing-site activity as the tactic evolved, with activity observed across many countries and in multiple languages. Acronis Threat Research Unit report described the broader campaign and its steganography-driven delivery chain.
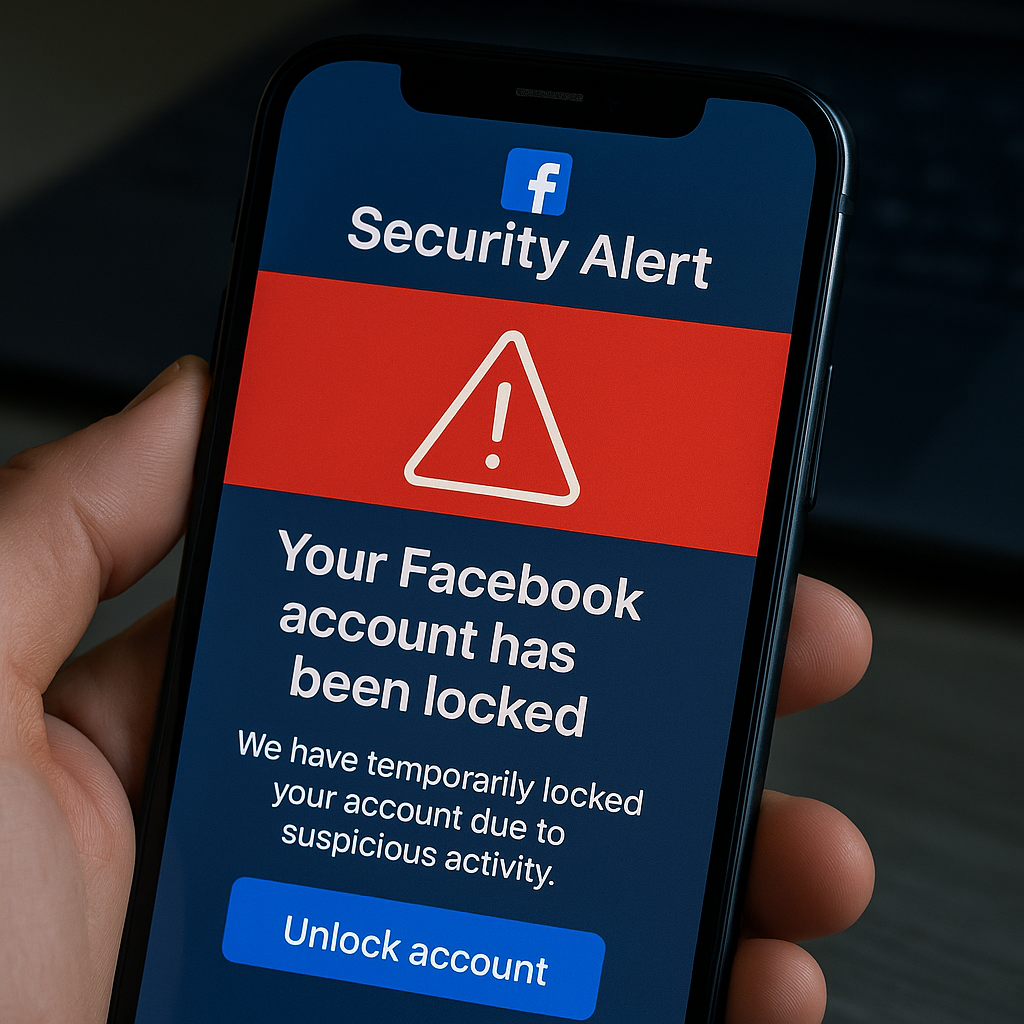
Researchers said the phishing workflow begins with a counterfeit Facebook security alert claiming someone has reported the user’s account and that it would be suspended within seven days. Victims are prompted to click a link to a PDF file purportedly from Facebook and to paste a URL into a Windows Run dialog or File Explorer to view the file. In reality, the file path hides the malicious payload, and the attacker further misleads by inserting spaces to obscure the command in the address bar. The image used to seed the infection, often a JPG, is placed in the Temp folder to blend in with normal file activity.
The campaign’s payload chain culminates with a loader written in Go that first checks for a virtual machine or sandbox environment before decrypting and loading shellcode into memory. The shellcode then unpacks StealC version 2, a backdoor/infostealer capable of siphoning data from a wide range of applications, including major browsers and more than 20 cryptocurrency wallets. The loader also seeks credentials from cloud platforms and messaging, VPN, and database tools, such as OpenVPN and Proton VPN. The StealC variant referenced is discussed in a related security write-up describing its enhanced stealth and data-theft features.
Analysts identified a second-stage component delivered via a plaintext PowerShell payload embedded within the image, designed to give attackers flexibility to change dropped files without modifying the initial phishing site. A Go-based loader then decrypts and loads the shellcode into memory, enabling the theft of credentials and keys across a broad set of software and services. The incident highlights the evolving nature of social-engineering campaigns and the persistence of StealC as a default final payload in modern attack chains.
Researchers also noted that the attackers have shifted away from controlling traditional malicious domains to hosting image-based payloads on platforms such as Bitbucket, an approach intended to complicate detection and takedown efforts. The campaign’s carry-through, including global distribution and language variation, underscores a broader trend highlighted by security firms that such social-engineering tactics are surging. In recent threat reports, observers have quantified the rise of these interventions, with ESET reporting a 517 percent increase in similar attacks over six months, positioning them as the second most common attack vector behind phishing.
Industry researchers, including Acronis’ Kimhy, say FileFix and its kin are evolving rapidly, and they expect further variants to surface as attackers refine their infrastructure. Kimhy described the campaign’s architecture as a refined, modular “plane” that attackers continually upgrade, including new delivery methods and payloads. He also stressed that defeating these threats requires stronger anti-phishing training and user awareness about the possibility of legitimate-looking prompts leading to malware. Proofpoint analysis of ClickFix-style social engineering notes the broader threat landscape that FileFix is now part of.