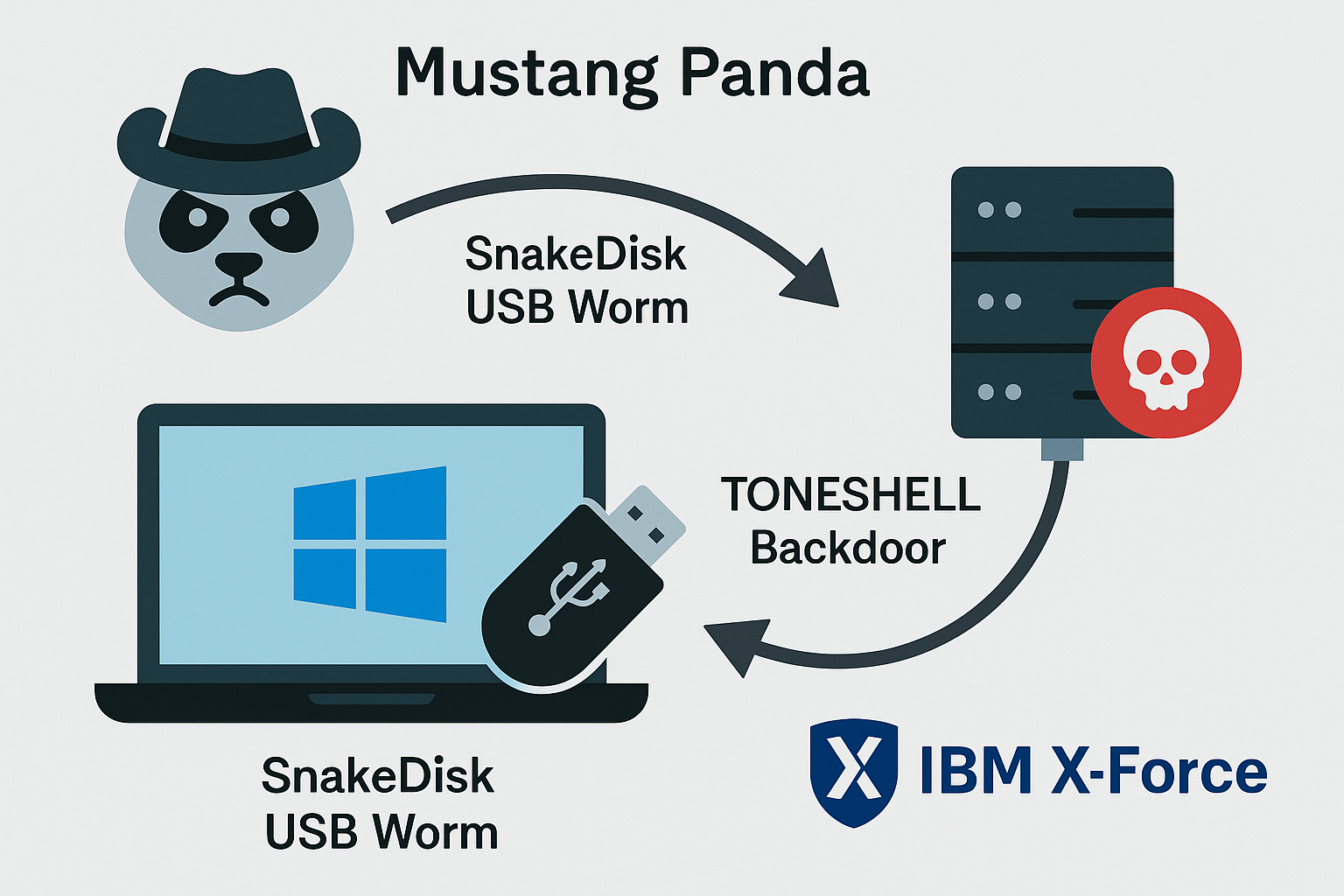
The China-aligned threat actor Mustang Panda, tracked by IBM X-Force as Hive0154, has been observed deploying an updated version of the TONESHELL backdoor alongside a newly identified USB worm named SnakeDisk, according to a recent IBM analysis. The researchers describe the cluster as a mature, multi-faceted operation active since at least 2012.
TONESHELL8 and TONESHELL9, the newly identified variants described by IBM X-Force, support command-and-control communication through locally configured proxy servers to blend in with enterprise traffic and enable two active reverse shells in parallel. The malware also incorporates junk code copied from OpenAI’s ChatGPT to hinder static detection and analysis, the researchers noted.
A related development is SnakeDisk, a USB worm launched in tandem with TONESHELL. The worm shares overlaps with TONEDISK (also known as WispRider), another USB-worm framework under the TONESHELL family. It primarily detects USB devices connected to a host and propagates by moving existing files on the drive into a new sub-directory and renaming them to USB.exe to entice victims to click the payload on a new machine. Once executed, the files are copied back to their original locations.
SnakeDisk is geofenced to execute only on public IP addresses geolocated to Thailand, a constraint that underscores the actor’s focus on a specific geography. The malware also serves as a conduit to drop Yokai, a backdoor that provides a reverse shell for executing arbitrary commands. Yokai was previously detailed by security researchers in December 2024 in intrusions targeting Thai officials.
IBM notes that Yokai shows overlaps with other backdoor families attributed to Hive0154, such as PUBLOAD/PUBSHELL and TONESHELL. Although these families are distinct components of the broader ecosystem, they roughly follow the same structure and use similar techniques to establish a reverse shell with their C2 servers. The use of SnakeDisk and Yokai likely points to a sub-group within Mustang Panda that is highly focused on Thailand, while illustrating the ongoing evolution and refinement of the threat actor’s malware arsenal.
IBM’s analysts highlighted the cluster’s breadth and the persistence of Hive0154 as a growing and continually developing threat actor. The company emphasized that the group maintains a sizable malware ecosystem with frequent overlaps in code, techniques, and targeting.