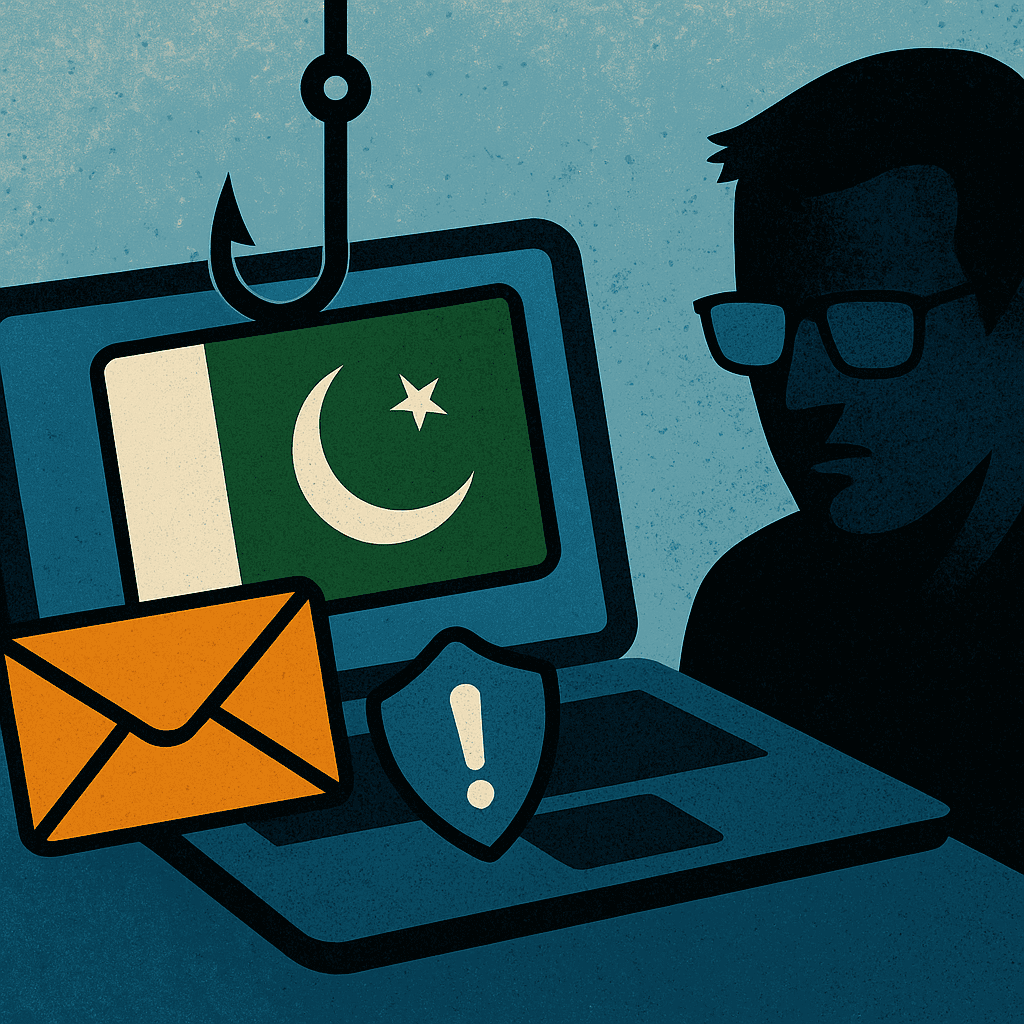
Security researchers say a hacking group known as Confucius has run a phishing campaign against targets in Pakistan that deployed information stealers and a Python backdoor, including malware families identified as WooperStealer and Anondoor, according to what Fortinet FortiGuard Labs researcher Cara Lin said.
The group is believed to have been active since 2013 and to operate across South Asia, and has repeatedly targeted government agencies, military organizations, defense contractors and critical industries using spear-phishing and malicious documents as initial access vectors, the article said.
Fortinet documented multiple attack chains aimed at Pakistani users, including a December 2024 campaign that used a .PPSX file to trigger WooperStealer via DLL side-loading, a March 2025 wave that used Windows shortcut (.LNK) files to launch a WooperStealer DLL, and an August 2025 .LNK that sideloaded a DLL which deployed Anondoor, a Python implant that gathers system information, takes screenshots, enumerates files and can dump Google Chrome passwords.
Seebug’s KnownSec 404 Team previously documented the use of Anondoor in July 2025, and security firms say the shift from information‑stealers toward a backdoor likely signals a move by the actor toward longer‑term monitoring and persistence.
Fortinet researchers said the actor has layered obfuscation techniques to evade detection and has shown the ability to pivot rapidly between techniques, infrastructure and malware families to maintain operational effectiveness, according to the article.
Separately, K7 Security Labs described an infection sequence linked to a different group, Patchwork, that begins with a malicious macro that downloads a .LNK file containing PowerShell code to fetch additional payloads and use DLL side‑loading to launch the primary malware, while displaying a decoy PDF. The company said the final payload connects to a command‑and‑control server, gathers system information, retrieves encoded instructions decrypted for execution and is capable of taking screenshots and uploading and downloading files.
K7 also said the malware can retry exfiltration for a configurable period and will attempt to resend data up to 20 times; the article does not disclose how many organizations or individuals were affected.