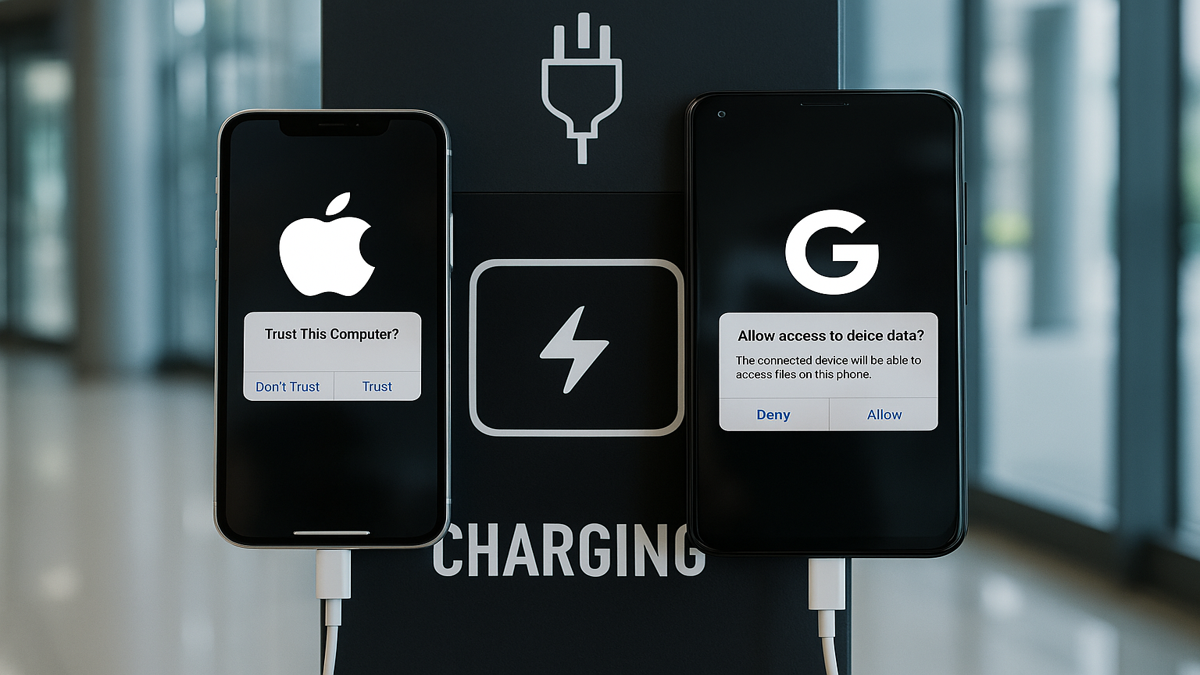
In a groundbreaking study, researchers have identified a new attack method known as ChoiceJacking, which exploits vulnerabilities in the defenses against juice jacking on both iOS and Android platforms. This attack poses a significant risk to mobile device security, allowing malicious chargers to autonomously spoof user input and access sensitive data without user consent.
The term “jujce jacking” originated a decade ago during a Defcon security conference, where the potential for malicious chargers to steal data became evident. Apple and Google implemented countermeasures requiring user confirmation before a charger could access a device’s files. However, this new research reveals that these defenses have fundamental flaws that attackers can easily bypass.
The Graz University of Technology’s findings indicate that the underlying assumption of USB protocols—that attackers cannot inject input events while establishing a data connection—is incorrect. Their research presented at the upcoming Usenix Security Symposium outlines three methods by which ChoiceJacking can circumvent traditional juice jacking defenses.
Reacting to the alarming findings, Apple has made changes to their iOS confirmation dialogs, which now require user authentication via PIN or password. Google updated its security measures in Android version 15 as part of an ongoing effort to bolster mobile security. Nonetheless, the fragmented nature of the Android ecosystem leaves many devices vulnerable to these types of attacks.
In light of these revelations, tech experts are urging users to remain cautious, particularly when using public charging stations. Federal authorities have consistently warned against the risks associated with public charging, and while practical attacks have not been documented, the emergence of ChoiceJacking calls for increased awareness among consumers.
The vulnerabilities related to ChoiceJacking are documented as CVE-2025-24193 for Apple and CVE-2024-43085 for Google, among others. Despite the patching efforts by major manufacturers, many Android devices remain at risk, especially for those with USB debugging enabled, offering potential routes for attackers to gain deeper access to user data.