Cybercrime
-
TA558 Deploys AI-Generated Scripts to Deliver Venom RAT, Targeting Hotels in Latin America
Kaspersky links TA558’s latest activity to the RevengeHotels cluster, where attackers use AI-generated scripts to deliver Venom RAT to hotels in Latin America through phishing emails, with goals including stealing guest credit card data and expanding their reach via AI-assisted phishing.
-
TA415 Uses Visual Studio Code Remote Tunnels in Targeted U.S.-China Policy Espionage Campaign
A China-aligned threat actor known as TA415 carried out spear-phishing campaigns targeting U.S. policy and economic-relations circles, using VS Code Remote Tunnels and a Python loader, WhirlCoil, to establish a persistent backdoor and harvest data amid ongoing U.S.-China trade talks, according to Proofpoint.
-
Microsoft, Cloudflare Lead Disruption of RaccoonO365 Phishing Network, Seizing 338 Domains
Microsoft and Cloudflare led a coordinated takedown of the RaccoonO365 phishing-as-a-service network, seizing 338 domains and disrupting a campaign that had targeted thousands of Microsoft 365 credentials across dozens of countries. The operation highlights how criminal networks leverage legitimate internet infrastructure to facilitate credential theft, with law enforcement pursuing principal operators and affiliates alike.
-
Self-propagating npm supply-chain attack hits at least 187 packages in ‘Shai-Hulud’ worm
Security researchers warn of a self-propagating supply-chain attack on npm that has compromised at least 187 packages in a campaign dubbed ‘Shai-Hulud.’ The worm begins with the widely used @ctrl/tinycolor package and spreads to other maintainers’ packages, using a bundle.js payload that leverages TruffleHog to exfiltrate secrets and forge GitHub Actions workflows.
-
Kering confirms data breach hits Gucci, Balenciaga and Alexander McQueen; customer records exposed
Kering says hackers accessed customer data in a June 2025 breach affecting Gucci, Balenciaga and Alexander McQueen, exposing names, birth dates, phone numbers, emails and purchase histories, but not payment card data. The incident has been linked to the ShinyHunters group via Salesforce CRM access, with law enforcement reporting arrests in Paris. Authorities warn of…
-
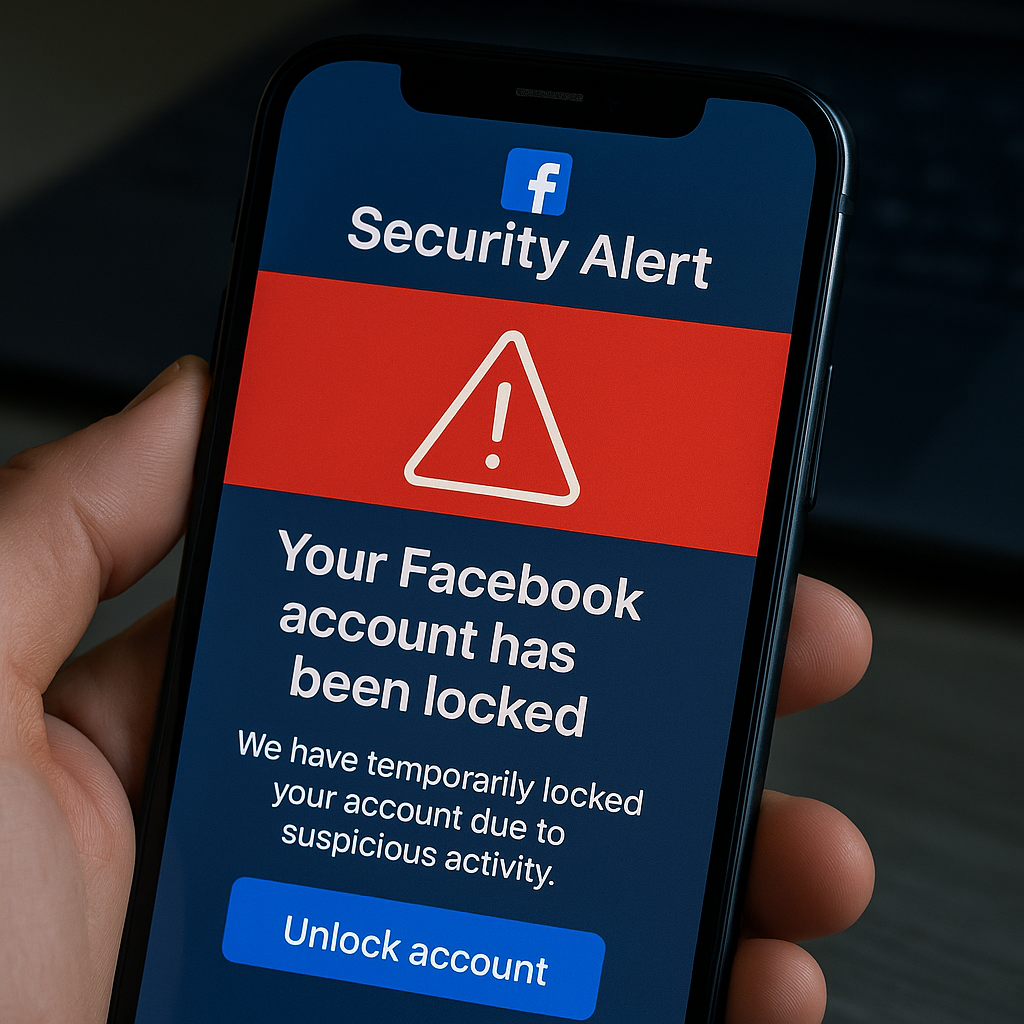
FileFix: New Facebook security alert spoof hijacks victims into downloading StealC infostealer, researchers warn
Security researchers have uncovered a campaign dubbed FileFix that masquerades as a Facebook security alert to trick users into executing a malicious payload, culminating in the StealC infostealer. The operation, a variant of the ClickFix social-engineering technique, shows global reach, steganography-based delivery, and a Go-based loader that drops StealC v2, with researchers noting evolving infrastructure…
-
KillSec ransomware hits Brazil’s healthcare IT supply chain, exposing tens of thousands of records
KillSec has claimed responsibility for a September 2025 attack on Brazil’s healthcare software provider MedicSolution, breaching the healthcare IT supply chain and exposing more than 34 GB of sensitive health data across clinics and laboratories, including medical and minor records.
-
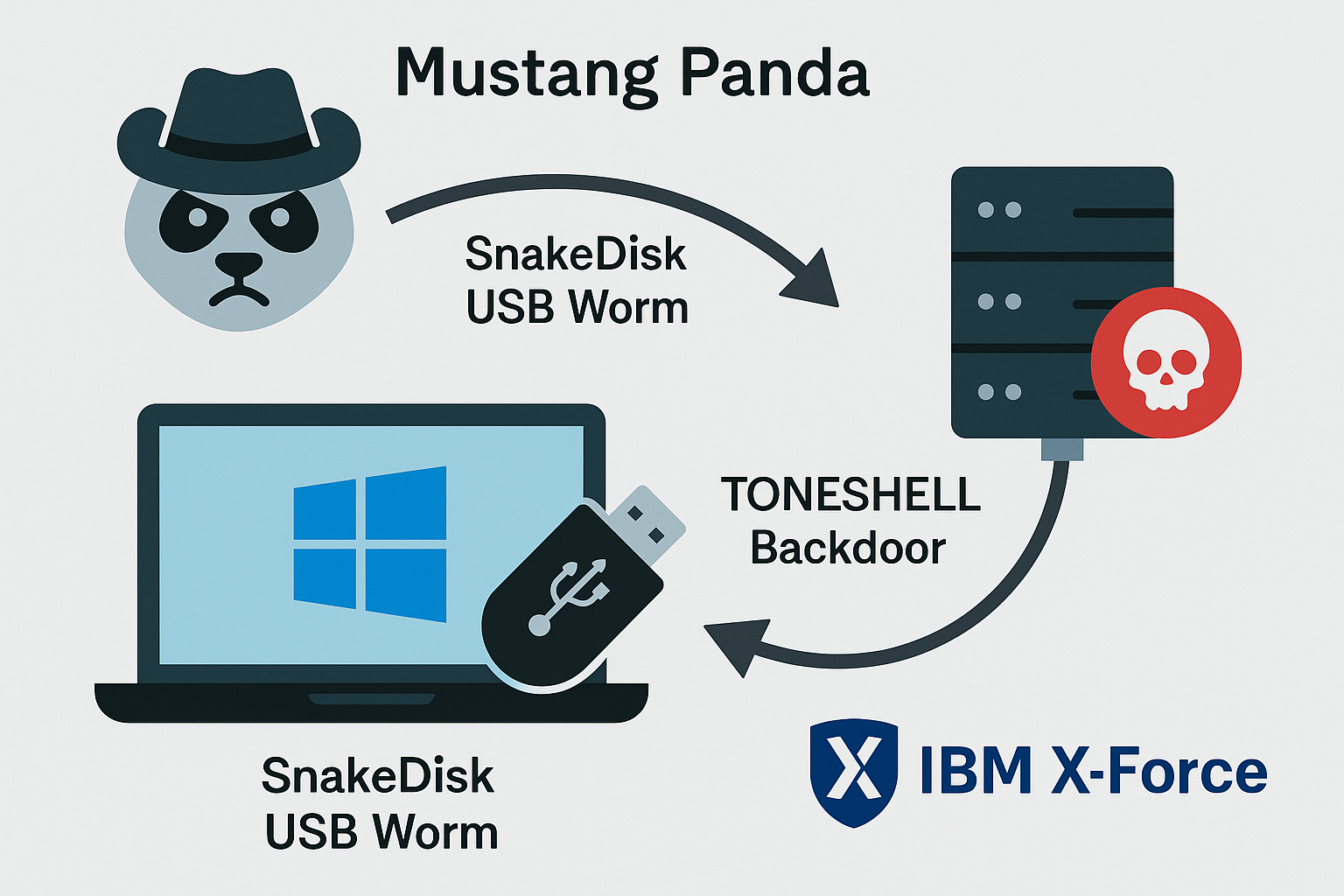
Mustang Panda Deploys SnakeDisk USB Worm and Updated TONESHELL Backdoor, IBM X-Force Warns
IBM X-Force reports that the Mustang Panda group has deployed an updated TONESHELL backdoor alongside a new USB worm named SnakeDisk, with SnakeDisk geofenced to Thailand and capable of dropping Yokai, a reverse-shell backdoor. The investigation highlights ongoing evolution within Hive0154 and a focus on targeted regional operations.