AI Vulnerabilities
-
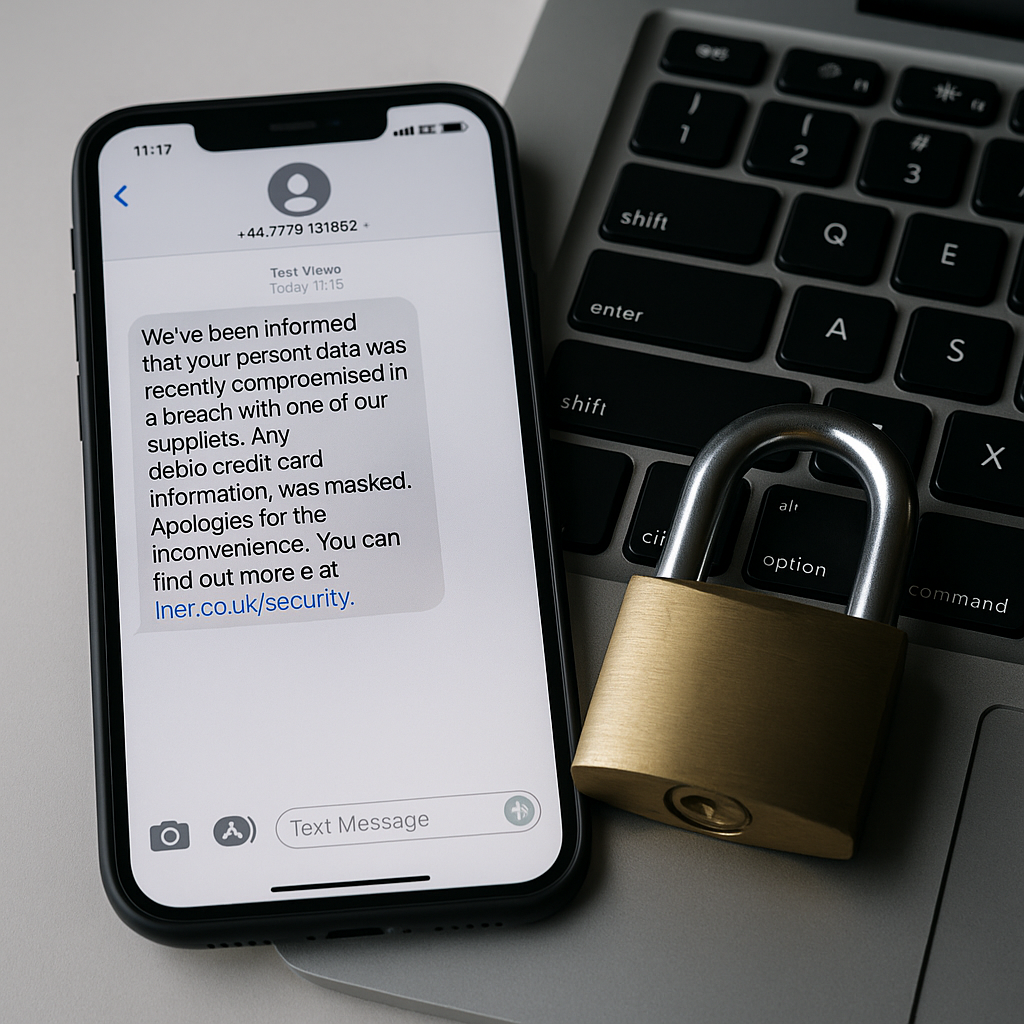
LNER confirms customer data accessed in third-party data breach
London North Eastern Railway says customer contact details and some journey information were accessed via a third-party supplier, with no impact on ticketing or services and no storage of bank data. The company urges caution on phishing and emphasizes secure passwords.
-
CISA Adds D-Link Wi-Fi Camera Vulnerabilities to Known Exploited Catalog Amid Active Threats
CISA has added three vulnerabilities affecting D-Link Wi-Fi cameras and video recorders to its KEV catalog amid warnings of active exploitation. Users are urged to take action as fixes for some issues have already been released.
-
Critical Vulnerabilities Discovered in NVIDIA’s Triton Inference Server
A set of critical vulnerabilities in NVIDIA’s Triton Inference Server has been discovered, posing significant risks to organizations using the platform for AI operations. Potential exploits could lead to remote control of servers and theft of sensitive data.
-
Significant Vulnerabilities Discovered in Tridium’s Niagara Framework
Researchers have discovered multiple critical vulnerabilities in Tridium’s Niagara Framework, a platform widely used in building management, which could allow attackers to compromise systems on the same network. These vulnerabilities have high CVSS scores and can lead to unauthorized access and operational disruptions.
-
Sam Altman Sounds Alarm on AI Threats to Financial Security at Federal Reserve Event
Sam Altman, CEO of OpenAI, warns financial leaders about the dangers of relying on outdated authentication methods during a speech at a Federal Reserve event, stressing the need for reform in financial security practices amidst advancing AI technology.
-
Critical Cisco ISE Vulnerability Allows Pre-Authentication Command Execution
Cisco has issued an urgent advisory regarding a critical vulnerability in its Identity Services Engine (ISE) that allows unauthorized command execution. Rated 10/10 in severity, it was discovered by Kentaro Kawane and reported via Trend Micro. Cisco emphasizes the need for immediate action.
-
Security Flaw Exposes Hundreds of Laravel Applications to Remote Code Execution
A vulnerability affecting over 600 Laravel applications has been discovered, allowing the exploitation of leaked APP_KEYs to gain remote code execution capabilities. Cybersecurity experts emphasize the importance of immediate key rotation and continuous monitoring to prevent such security breaches.
-
Critical Remote Code Execution Vulnerability Discovered in mcp-remote Project
A critical vulnerability in the mcp-remote project could allow hackers to execute arbitrary operating system commands, prompting updates and stronger security practices for users.
-
AMD Issues Warning on New Transient Scheduler Vulnerabilities in Chipsets
AMD has issued a warning regarding new vulnerabilities termed Transient Scheduler Attacks (TSA) that could expose sensitive data across its chipsets, necessitating immediate attention and remedial updates.