Android malware
-
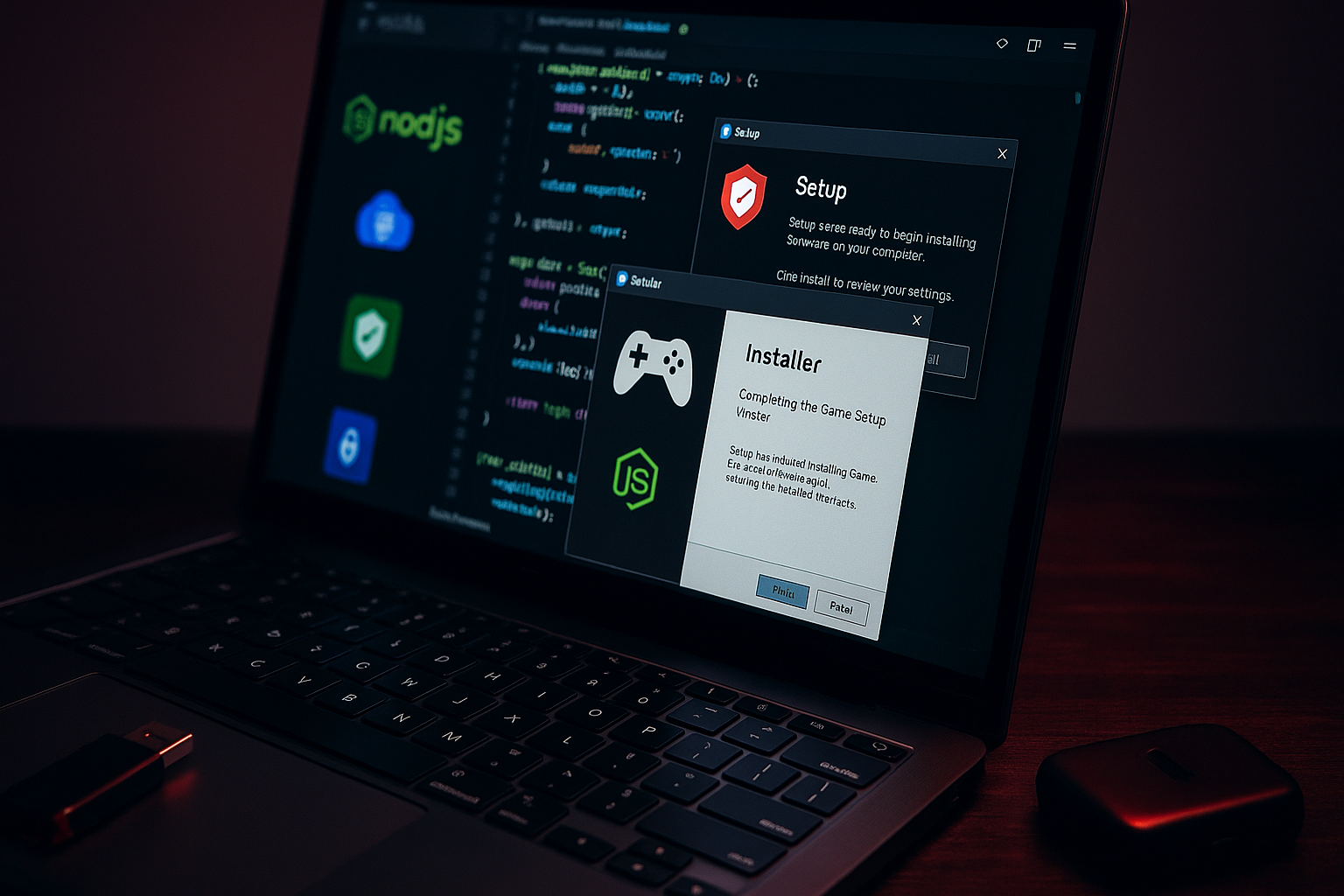
Researchers: Stealit malware uses Node.js single-executable feature to spread
Fortinet researchers said the Stealit malware campaign is abusing Node.js’ experimental Single Executable Application feature and, in some variants, Electron, to distribute stealers and a RAT via counterfeit installers on file‑sharing sites.
-
Ukraine agency says Russian-linked hackers used AI to aid cyber attacks in H1 2025
Ukraine’s SSSCIP said Russian-linked hackers increased use of AI in cyber attacks in H1 2025, recording 3,018 incidents and using AI-generated phishing and malware while exploiting webmail flaws and abusing legitimate cloud services.
-
ESET: Fake Signal and ToTok Android Apps used to deploy spyware in UAE
ESET researchers warned that two spyware campaigns in the UAE use fake Signal and ToTok Android apps disguised as plugins or add‑ons to collect contacts, messages, backups and files; the spyware has been traced to mid‑2022 and is blocked by Google Play Protect for devices with Google Play Services.
-
XWorm backdoor resurfaces with ransomware module and dozens of plugins
Researchers at Trellix told BleepingComputer that new XWorm variants 6.0, 6.4 and 6.5 are circulating in phishing campaigns, include more than 35 plugins and a ransomware module that encrypts user files and drops ransom instructions.
-
Trend Micro: SORVEPOTEL self‑propagating malware spreads via WhatsApp, hits Brazil hard
Trend Micro researchers said a self‑propagating malware campaign called SORVEPOTEL is spreading via WhatsApp and email to Windows desktops, concentrating in Brazil; it propagates through malicious ZIP attachments and PowerShell, aims for rapid spread rather than data theft, and has led to mass spam and account suspensions.
-
Malicious PyPI package ‘soopsocks’ acted as SOCKS5 proxy and Windows backdoor, researchers say
Researchers say a PyPI package called soopsocks posed as a SOCKS5 proxy but included Windows backdoor capabilities, downloaded 2,653 times before removal; analysis attributes reconnaissance, privilege elevation, firewall changes and data exfiltration to a compiled executable and accompanying scripts.
-
Fake Microsoft Teams installers promoted in search ads deliver Oyster backdoor, researchers say
Search ads and SEO poisoning have been used to promote fake Microsoft Teams installers that deliver the Oyster backdoor to Windows machines, researchers said; the trojanized installer drops a DLL and creates a scheduled task for persistence.
-
Malicious Rust crates impersonating fast_log steal Solana and Ethereum wallet keys, researchers say
Cybersecurity researchers say two malicious Rust crates impersonating the fast_log logging library were used to harvest Solana and Ethereum wallet keys from source code, with Crates.io removing the packages and preserving logs for analysis after responsible disclosure.
-
GitHub outlines changes to harden npm after self-replicating worm incident
GitHub said a self-replicating “Shai-Hulud” worm compromised maintainer accounts and injected malicious post-install scripts into npm packages, and outlined changes including required 2FA, short-lived granular tokens and trusted publishing to harden npm’s supply chain.