Azure AD
-
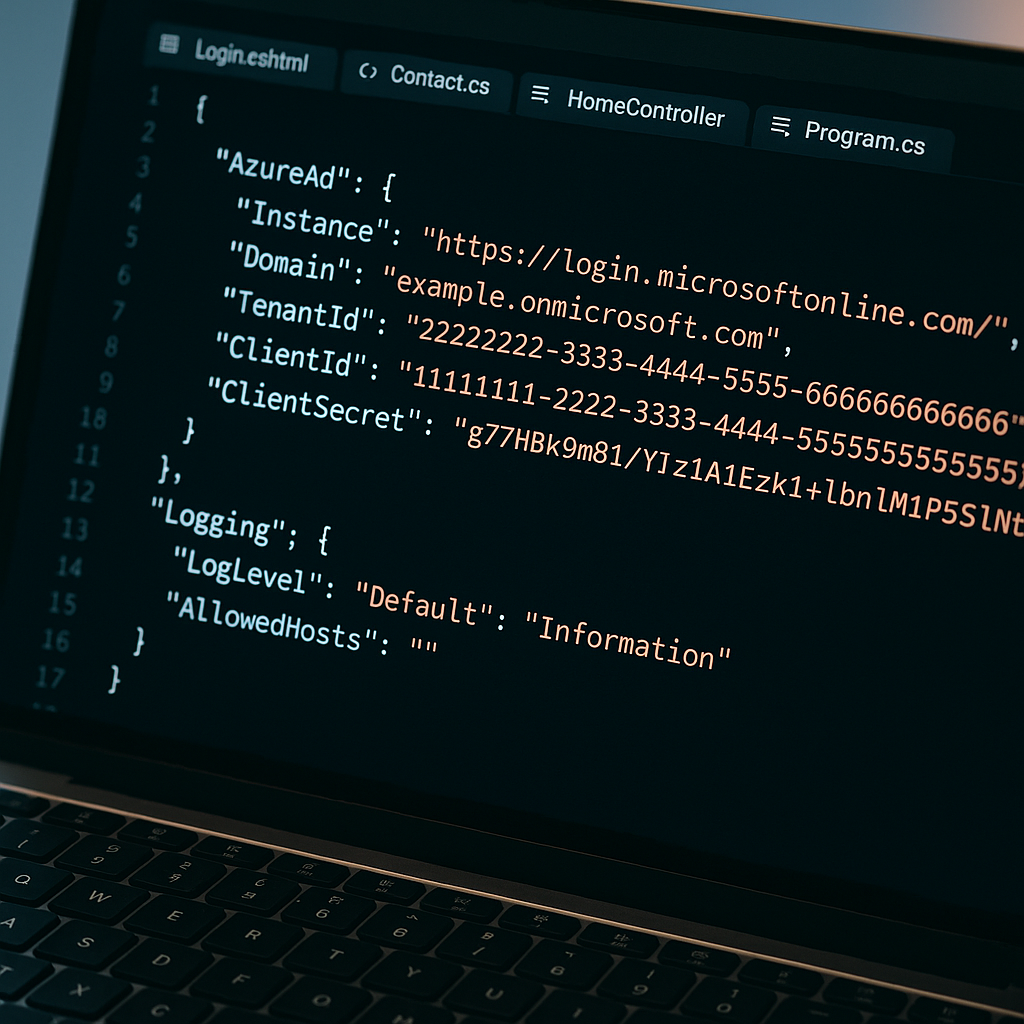
Public appsettings.json leak exposes Azure AD credentials, enabling potential cloud access
Researchers from Resecurity’s HUNTER team warn that a publicly accessible appsettings.json file leaked Azure AD credentials (ClientId and ClientSecret), potentially enabling attackers to authenticate via OAuth 2.0 and access an organization’s Azure cloud resources; the incident underscores the ongoing risk of cloud-secret exposure and the need for strong secret-management practices.
-
Storm-0501 Debuts Brutal Hybrid Ransomware Attack Chain, Microsoft Warns
Microsoft Threat Intelligence warns Storm-0501 has deployed a brutal hybrid ransomware chain, exploiting hijacked privileged accounts to pivot between on‑prem and cloud, exfiltrate data, delete backups and encrypt remaining cloud resources, pressuring victims to pay or face potential shutdown.
-
China-linked Murky Panda exploits cloud trust to move laterally, CrowdStrike finds
A CrowdStrike 2025 Threat Hunting Report finds a 136% increase in cloud intrusions, driven by Murky Panda’s use of zero-day exploits and, more notably, their manipulation of trusted cloud relationships to move from SaaS providers into downstream customer environments, with links to a February 2025 breach of Commvault’s Microsoft Azure cloud environment highlighted as a…
-
Hackers exploit trusted Microsoft redirects and ADFS to steal Microsoft 365 logins, researchers say
Researchers describe a phishing campaign that uses legitimate office.com redirects and a misconfigured Microsoft tenant with ADFS to harvest Microsoft 365 credentials, bypassing some security controls. The attack chain begins with a misleading Google ad for “Office 265,” redirects through Office to a phantom domain, and uses conditional access restrictions to conceal the page from…