callback phishing
-
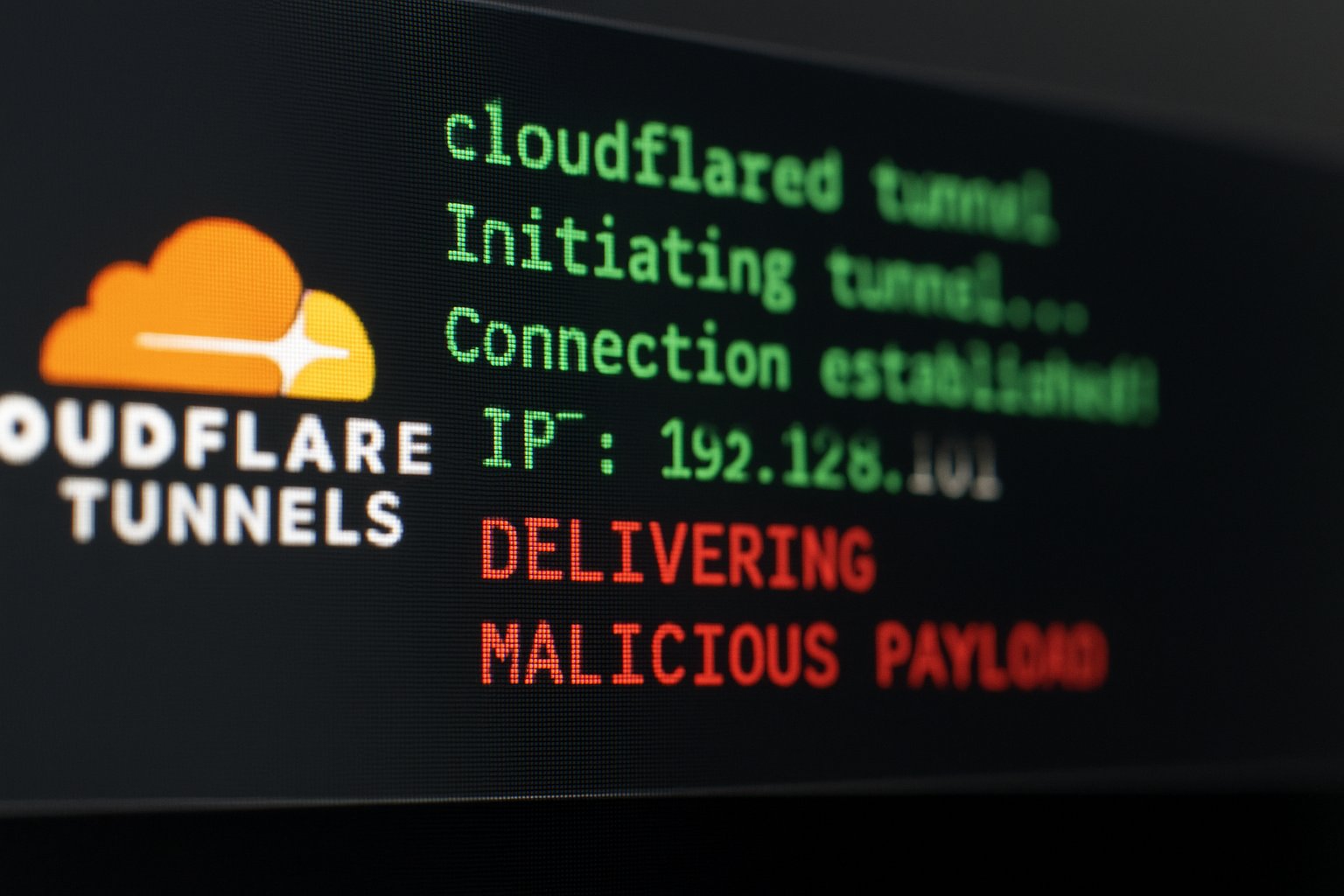
New Malware Campaign Exploits Cloudflare Tunnels to Deliver Malicious Payloads
A new malware campaign, codenamed SERPENTINE#CLOUD, is exploiting Cloudflare Tunnel subdomains to distribute malicious payloads via phishing emails. This sophisticated attack targets users across multiple regions and employs advanced techniques to evade detection.
-
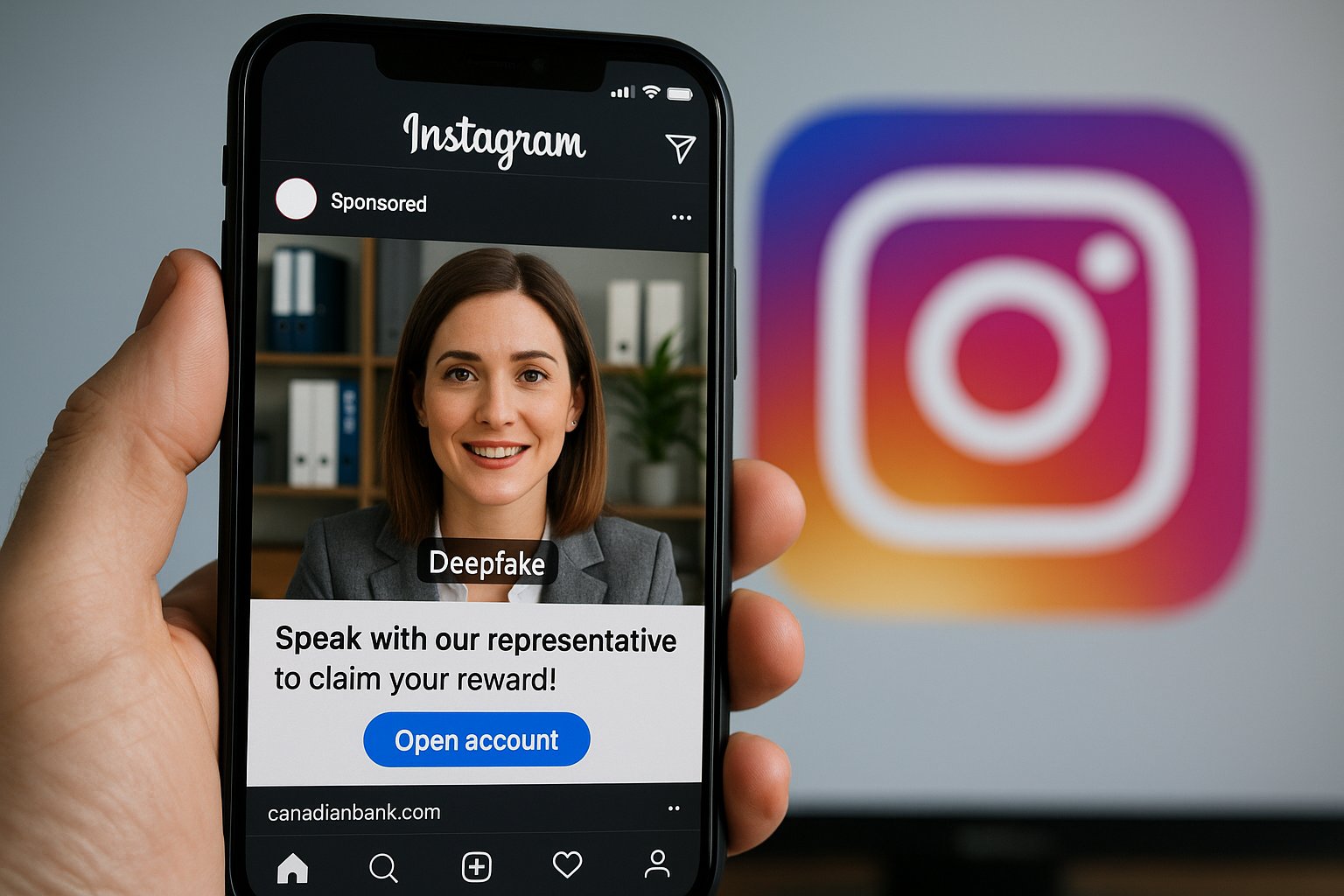
Fraudulent Instagram Ads Target Canadian Bank Customers with AI Deepfakes
Fraudulent Instagram ads impersonating financial institutions BMO and EQ Bank are targeting Canadian consumers with phishing scams involving AI deepfakes. These ads mislead users into providing personal information, prompting a response from affected banks and Meta’s commitment to investigate and remove fraudulent content.
-
Former Black Basta Affiliates Adapt Tactics Amid Ongoing Cyber Threats
Former members of the Black Basta ransomware operation have adapted their tactics, leveraging email phishing and Microsoft Teams phishing to gain access to networks. The report highlights the evolution of these cybercriminals even as the Black Basta brand faces challenges.
-
Rare Werewolf APT Targets Russian Entities with Sophisticated Cyber Attacks
Rare Werewolf, an advanced persistent threat (APT) group, is reported to have launched a series of cyber attacks targeting Russian and CIS entities, using legitimate software to enhance the stealth of their operations.
-
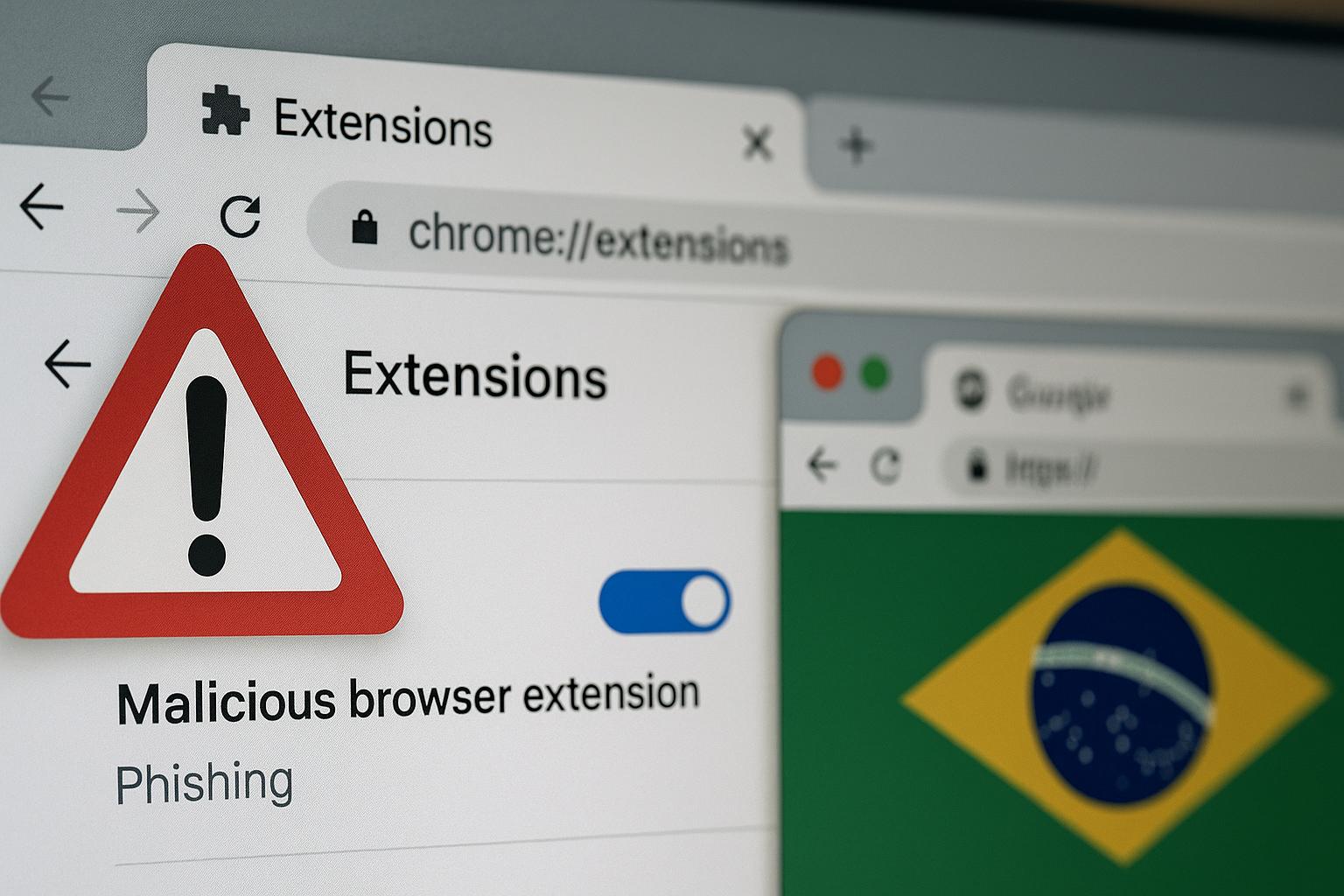
Cybersecurity Alert: Malicious Browser Extensions Target Brazilian Users in Widespread Phishing Campaign
A new phishing campaign has surfaced, aiming at Brazilian users through malicious browser extensions that stole sensitive authentication data. The operation has reportedly infected 722 systems across different countries.
-
FBI Warns Law Firms of Rising Cyber Threats from Silent Ransom Group
The FBI has warned U.S. law firms of a growing cyber threat from the Silent Ransom Group, which has increased its focus on the legal sector since early 2023, employing phishing tactics and social engineering calls to access sensitive legal data.
-
Cybercriminals Deploy Fake Ledger Apps to Steal Cryptocurrency Seed Phrases from macOS Users
Cybercriminals are increasingly using fake Ledger applications to steal seed phrases from macOS users, threatening their cryptocurrency assets. Reports from Moonlock Lab and Jamf highlight the evolution of these attacks, emphasizing the importance of downloading official applications and safeguarding sensitive data.
-
North Korean Konni APT Expands Phishing Attacks Targeting Ukraine
Konni APT, a North Korean threat actor, is reportedly conducting a phishing campaign aimed at Ukrainian government entities, signaling a strategic shift in its operations from Russia. The group aims to collect critical intelligence on the ongoing conflict, utilizing sophisticated phishing techniques and malware.