Google Threat Intelligence
-
Vane Viper identified as a major malvertising operator, DNS-driven adtech network linked to trillions of queries
A deep-dive by Infoblox, with Guardio and Confiant, accuses the threat actor Vane Viper of running a vast malvertising and adtech operation that generated about 1 trillion DNS queries across thousands of compromised sites. The network leverages push notifications and service workers to stay persistent, links to major adtech players like PropellerAds, and has expanded…
-
Security firm flags in-the-wild exploitation of Pandoc flaw CVE-2025-51591 to target AWS IMDS
Security researchers at Wiz have observed in-the-wild exploitation of CVE-2025-51591, a Pandoc flaw that enables SSRF against AWS EC2 IMDS, with attackers attempting to exfiltrate data via crafted iframes. The activity underscores the importance of IMDSv2 and least-privilege IAM roles to mitigate cloud credential exposure.
-
Iranian-linked hackers expand European operations with fake job portals and new malware, researchers say
Security researchers say Iranian government-backed attackers are targeting Western Europe with fake job portals and new Minibike malware, including MiniJunk and MiniBrowse, delivered through a multi-stage DLL sideloading chain. The operation focuses on Denmark, Portugal, and Sweden and appears linked to broader Iran-aligned threat activity.
-
TA558 Deploys AI-Generated Scripts to Deliver Venom RAT, Targeting Hotels in Latin America
Kaspersky links TA558’s latest activity to the RevengeHotels cluster, where attackers use AI-generated scripts to deliver Venom RAT to hotels in Latin America through phishing emails, with goals including stealing guest credit card data and expanding their reach via AI-assisted phishing.
-
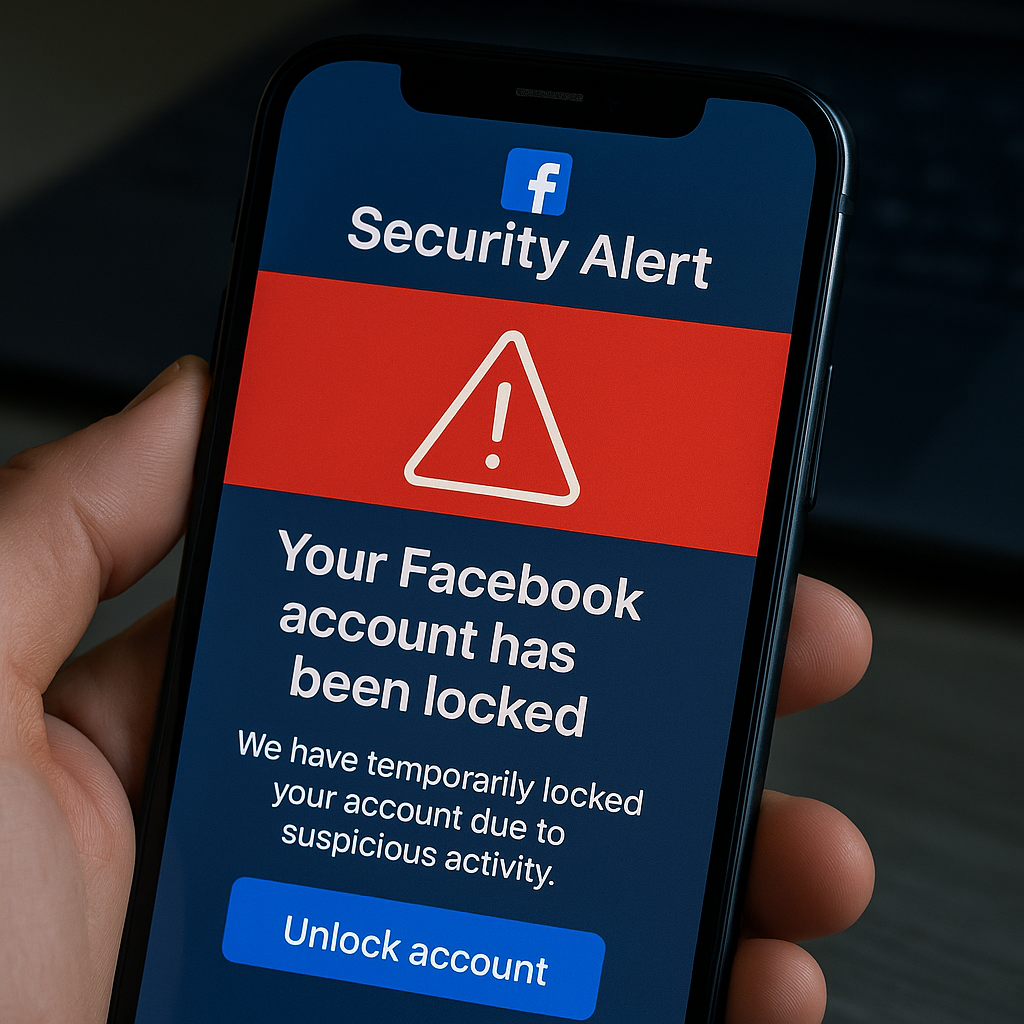
FileFix: New Facebook security alert spoof hijacks victims into downloading StealC infostealer, researchers warn
Security researchers have uncovered a campaign dubbed FileFix that masquerades as a Facebook security alert to trick users into executing a malicious payload, culminating in the StealC infostealer. The operation, a variant of the ClickFix social-engineering technique, shows global reach, steganography-based delivery, and a Go-based loader that drops StealC v2, with researchers noting evolving infrastructure…
-
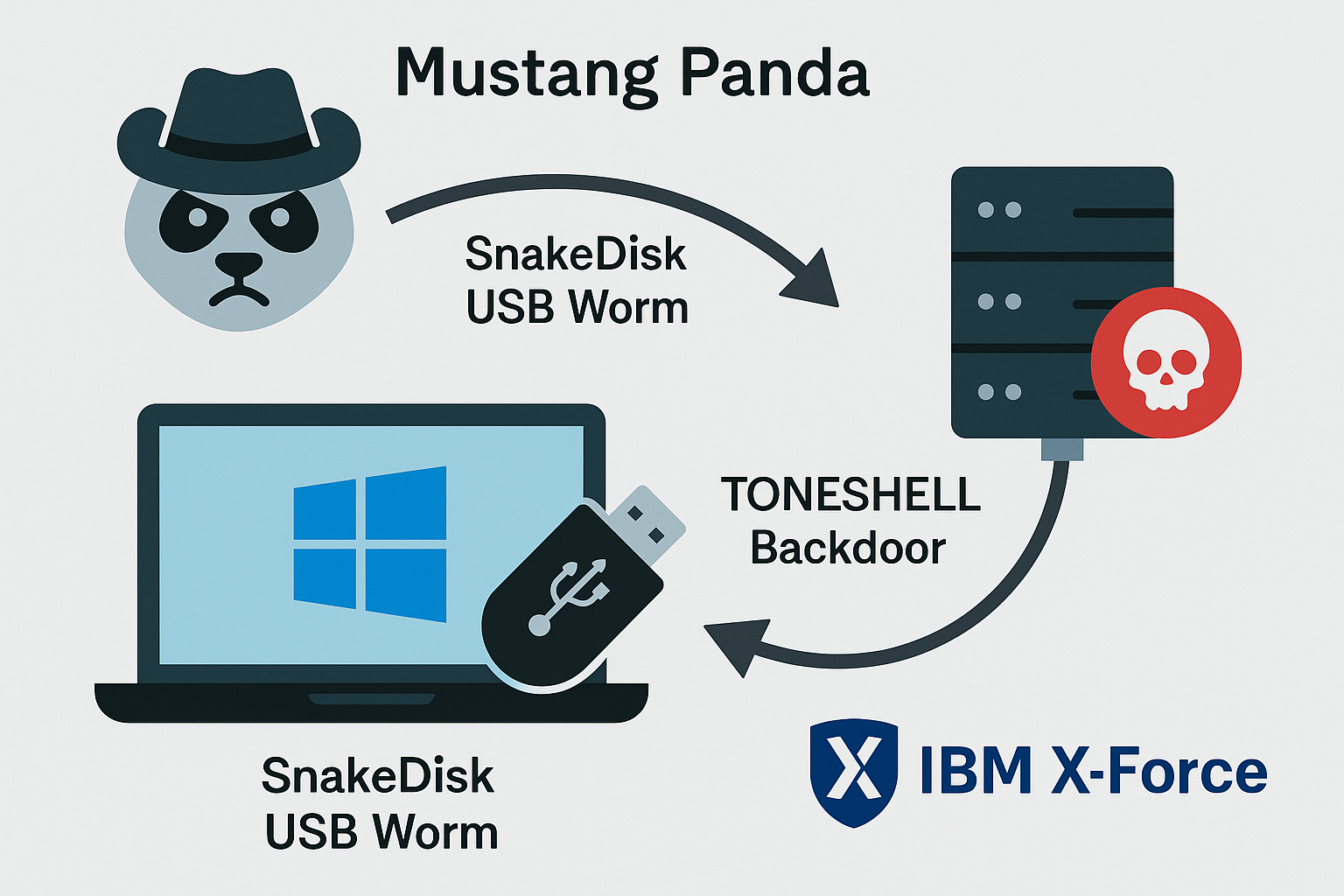
Mustang Panda Deploys SnakeDisk USB Worm and Updated TONESHELL Backdoor, IBM X-Force Warns
IBM X-Force reports that the Mustang Panda group has deployed an updated TONESHELL backdoor alongside a new USB worm named SnakeDisk, with SnakeDisk geofenced to Thailand and capable of dropping Yokai, a reverse-shell backdoor. The investigation highlights ongoing evolution within Hive0154 and a focus on targeted regional operations.
-
Backdoor.Win32.Buterat Targets Government and Enterprise Networks, Researchers Say
A new analysis from Point Wild details Buterat, a long-running backdoor that targets government and enterprise networks. The malware uses thread manipulation and encrypted C2 channels to avoid detection and maintain persistence, with defenders urged to strengthen endpoints and employee training.
-
VirusTotal flags 44 undetected SVGs in Colombian phishing campaign; hundreds of SVGs detected in the wild
VirusTotal has flagged a new malware campaign using 44 undetected SVG files to phish as Colombia’s Fiscalía General de la Nación, injecting a Base64-encoded HTML page and triggering a hidden ZIP download. Overall SVG detections in the wild have reached 523, with earliest samples dating to August 14, 2025.
-
Palo Alto Networks says Salesforce data exposed in breach tied to Salesloft Drift supply-chain attack
Palo Alto Networks disclosed a data breach linked to a broader Salesloft Drift supply-chain attack that exposed customer data in its Salesforce CRM. The incident involved OAuth token abuse, mass exfiltration of Salesforce records, and credential harvesting, prompting token revocation, Drift disablement, and guidance for customers to review logs and rotate secrets.