Patch Management
-
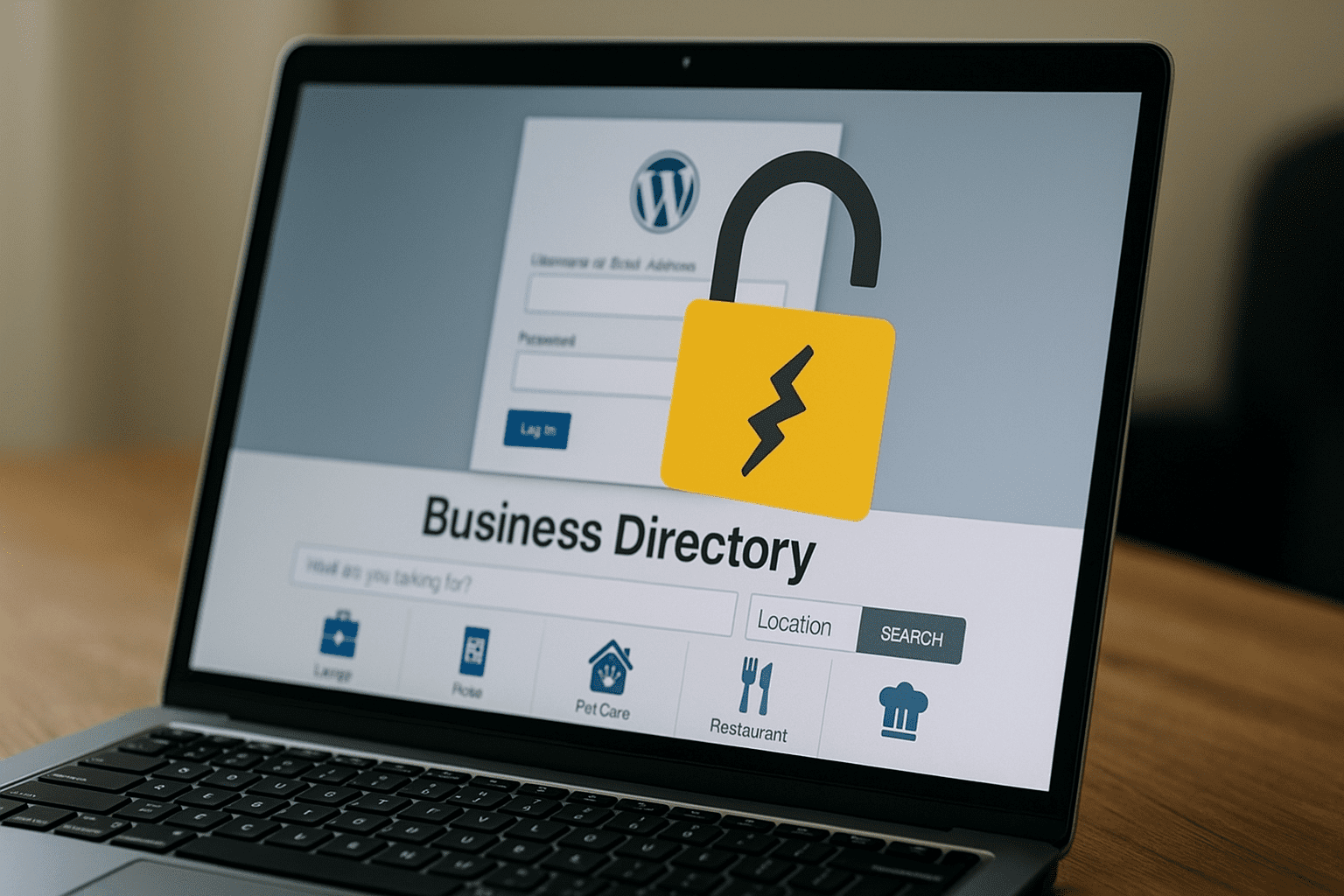
Attackers exploiting critical auth-bypass flaw in Service Finder WordPress theme
Security researchers at Wordfence say attackers are actively exploiting CVE-2025-5947, a critical authentication-bypass flaw in the Service Finder WordPress theme that can give attackers administrator access; a patch was released in version 6.1 and administrators are urged to update or stop using the theme.
-
Oracle issues emergency patch for critical E-Business Suite flaw tied to Cl0p attacks
Oracle issued an emergency update for a critical E-Business Suite vulnerability, CVE-2025-61882 (CVSS 9.8), which the article said has been exploited in recent Cl0p data thefts; Oracle and Mandiant have urged organisations to apply fixes and investigate possible prior compromise.
-
State-backed hackers exploited Libraesva ESG flaw; vendor issues urgent patch
Libraesva disclosed a state-sponsored exploitation of a vulnerability in its Email Security Gateway (ESG), tracked as CVE-2025-59689. The flaw, a command injection triggered by specially crafted compressed attachments, affects ESG versions 4.5 through 5.5.x before 5.5.7. Patches are available, and end-of-support for older builds mandates manual upgrades.
-
Fortra patches critical GoAnywhere MFT flaw; admins urged to restrict internet exposure of Admin Console
Fortra has issued patches for a critical GoAnywhere MFT vulnerability (CVE-2025-10035) that could enable remote command injection via deserialization. The company urges administrators to secure Admin Console access and apply the latest updates, as Shadowserver tracks hundreds of GoAnywhere instances and exposure continues to be a concern.
-
NIST Revamps Security Controls to Tighten Software Updates and Patch Management
NIST has revised its Security and Privacy Control Catalog to strengthen software update and patch management, introducing changes aimed at better incident response, root-cause analysis, and cyber resiliency to reduce the window of exposure in software supply chains.
-
Static Tundra: Russia-linked group exploits Cisco flaw to maintain long-term access to global networks, researchers say
A Russian state-sponsored group known as Static Tundra has been quietly compromising network devices worldwide for over a decade, exploiting a seven-year-old Cisco vulnerability to steal data and maintain access, according to Cisco Talos Intelligence.
-
CISA Adds Two N-able N-central Vulnerabilities to KEV; MSP Patch Push Underway
U.S. authorities added two vulnerabilities in N-able N-central to the Known Exploited Vulnerabilities catalog, while noting no public exploitation has been reported. The flaws—CVE-2025-8875 (insecure deserialization) and CVE-2025-8876 (command injection)—require authentication and have been patched in N-central versions 2025.3.1 and 2024.6 HF2, with upgrades urged for on-premises deployments.
-
Zoom and Xerox patch critical Windows and FreeFlow Core flaws that could enable privilege escalation and remote code execution
Zoom and Xerox released patches for critical vulnerabilities in Zoom Clients for Windows and FreeFlow Core, including a high-severity privilege-escalation flaw (CVE-2025-49457) in Windows Zoom clients and two severe flaws in FreeFlow Core (CVE-2025-8355 and CVE-2025-8356) that could enable remote code execution, prompting enterprise patches and risk-mitigation guidance.
-
Cisco Issues Urgent Patches for Critical Vulnerabilities in Cloud Services
Cisco has issued patches for critical vulnerabilities in its Identity Services Engine (ISE) and Customer Collaboration Platform (CCP), warning of potential exploits that could allow unauthorized access and disruption of services in cloud deployments.