PowerShell
-
New FileFix Variant Uses Cache Smuggling to Evade Security, Researchers Say
A new FileFix phishing variant uses cache smuggling to store a malicious ZIP in browser cache and run it via a hidden PowerShell command, letting it evade many security products, researchers said.
-
Trend Micro: SORVEPOTEL self‑propagating malware spreads via WhatsApp, hits Brazil hard
Trend Micro researchers said a self‑propagating malware campaign called SORVEPOTEL is spreading via WhatsApp and email to Windows desktops, concentrating in Brazil; it propagates through malicious ZIP attachments and PowerShell, aims for rapid spread rather than data theft, and has led to mass spam and account suspensions.
-
Malicious PyPI package ‘soopsocks’ acted as SOCKS5 proxy and Windows backdoor, researchers say
Researchers say a PyPI package called soopsocks posed as a SOCKS5 proxy but included Windows backdoor capabilities, downloaded 2,653 times before removal; analysis attributes reconnaissance, privilege elevation, firewall changes and data exfiltration to a compiled executable and accompanying scripts.
-
ESET: Gamaredon and Turla Coordinating Campaign Targets Ukrainian Institutions, Deploying Kazuar Backdoor
Security researchers have identified a coordinated campaign between Gamaredon and Turla targeting Ukrainian entities, with Kazuar backdoor deployments signaling active collaboration and evolving tactics across multiple campaigns in early 2025.
-
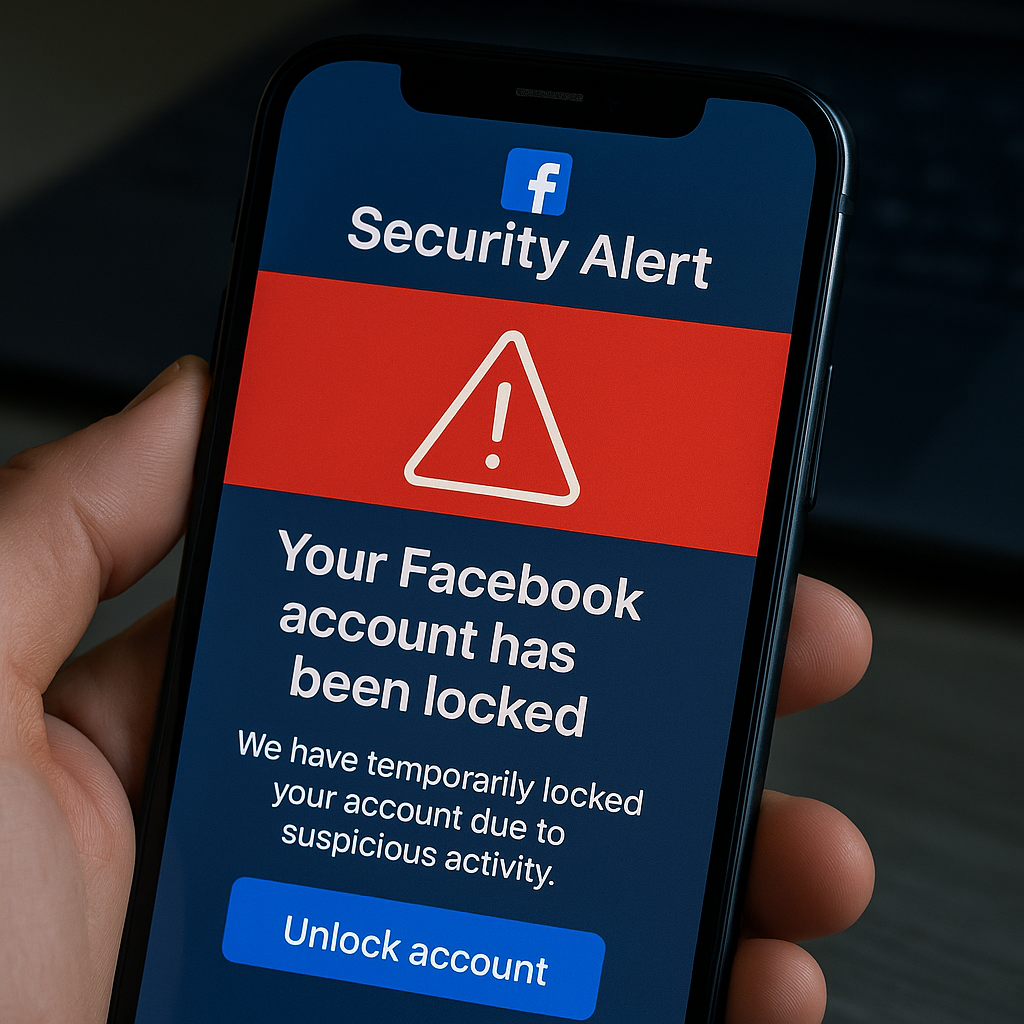
FileFix: New Facebook security alert spoof hijacks victims into downloading StealC infostealer, researchers warn
Security researchers have uncovered a campaign dubbed FileFix that masquerades as a Facebook security alert to trick users into executing a malicious payload, culminating in the StealC infostealer. The operation, a variant of the ClickFix social-engineering technique, shows global reach, steganography-based delivery, and a Go-based loader that drops StealC v2, with researchers noting evolving infrastructure…
-
ScarCruft Uses RokRAT in HanKook Phantom Campaign Targeting South Korea
Researchers have uncovered a targeted phishing campaign by North Korea-linked ScarCruft (APT37), dubbed Operation HanKook Phantom, delivering RokRAT to South Korean academics, former officials, and researchers via a manipulated LNK attack chain and PowerShell-based payloads, with exfiltration to multiple cloud services and a willingness to use decoy documents tied to high-profile statements.
-
State-sponsored XenoRAT campaign targets South Korean embassies, researchers say
A Trellix-led analysis describes a multi-phase, state-sponsored XenoRAT espionage campaign targeting South Korean embassies, with links to North Korea’s Kimsuky and indications of possible China-based sponsorship. The operation has conducted at least 19 spearphishing attacks since March, delivering XenoRAT via password-protected ZIP archives and complex, multilingual lures.