Research
-
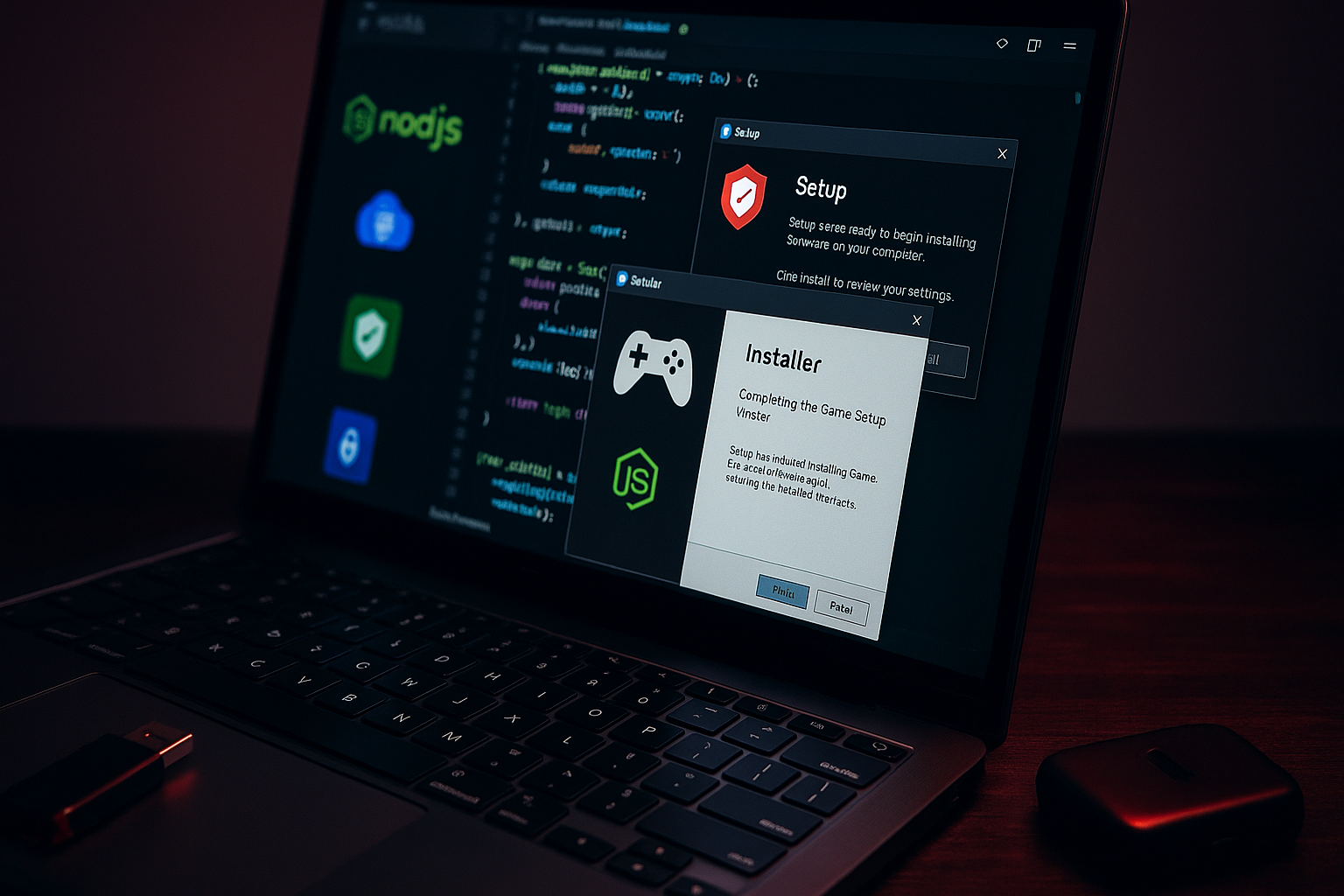
Researchers: Stealit malware uses Node.js single-executable feature to spread
Fortinet researchers said the Stealit malware campaign is abusing Node.js’ experimental Single Executable Application feature and, in some variants, Electron, to distribute stealers and a RAT via counterfeit installers on file‑sharing sites.
-
Researchers say low-cost DDR4 interposer can bypass Intel and AMD memory protections
Researchers at KU Leuven and the University of Birmingham say a low-cost DDR4 interposer called Battering RAM can redirect physical addresses to bypass Intel SGX and AMD SEV-SNP protections in cloud confidential computing, potentially allowing plaintext reads, data corruption and persistent backdoors.
-
Google to Consolidate Search Domains, Increasing Global Accessibility
Google has announced the retirement of separate country code domains for search, unifying them under Google.com to enhance user experience, though some challenges remain regarding localized search results.
-
OpenAI Expands Bug Bounty Program and Cybersecurity Initiatives
OpenAI has announced expansions to its bug bounty and cybersecurity grant programs, including a significant increase in the maximum bug bounty payout from $20,000 to $100,000 and new microgrants for innovative cybersecurity research proposals.