Android malware
-
GitHub Tightens npm Publishing Security with 2FA, Short-Lived Tokens and Trusted Publishing
GitHub announced a sweeping set of security measures for npm publishing, including deprecating legacy tokens, migrating to FIDO-based 2FA, and introducing seven-day, short-lived granular tokens plus trusted publishing that uses OpenID Connect and cryptographic provenance attestations to bolster npm’s supply-chain security.
-
SEO-poisoning BadIIS malware tied to Operation Rewrite targets East and Southeast Asia, researchers say
Security researchers say a Chinese-speaking actor is using the BadIIS malware in an Operation Rewrite SEO-poisoning campaign to hijack search results via a compromised IIS proxy, targeting East and Southeast Asia with Vietnam as a focus.
-
FileFix: New Facebook security alert spoof hijacks victims into downloading StealC infostealer, researchers warn
Security researchers have uncovered a campaign dubbed FileFix that masquerades as a Facebook security alert to trick users into executing a malicious payload, culminating in the StealC infostealer. The operation, a variant of the ClickFix social-engineering technique, shows global reach, steganography-based delivery, and a Go-based loader that drops StealC v2, with researchers noting evolving infrastructure…
-
RatOn Android malware evolves into ATS-enabled remote access trojan, ThreatFabric says
ThreatFabric reports that RatOn has evolved from NFC relay attacks into an ATS-enabled Android remote access trojan, capable of automated cryptocurrency transfers, overlay ransomware-style screens, and NFC relay via NFSkate, with initial activity centered in the Czech Republic and Slovakia likely to follow.
-
18 npm Packages Published With Malware That Rewrites Crypto Destinations
Aikido Security reported that attackers pushed malicious updates to 18 npm packages on Sept. 8 that inject browser hooks to intercept and rewrite crypto transaction destinations; the company said maintainers were targeted via phishing and listed indicators including specific compromised package versions.
-
VirusTotal flags 44 undetected SVGs in Colombian phishing campaign; hundreds of SVGs detected in the wild
VirusTotal has flagged a new malware campaign using 44 undetected SVG files to phish as Colombia’s Fiscalía General de la Nación, injecting a Base64-encoded HTML page and triggering a hidden ZIP download. Overall SVG detections in the wild have reached 523, with earliest samples dating to August 14, 2025.
-
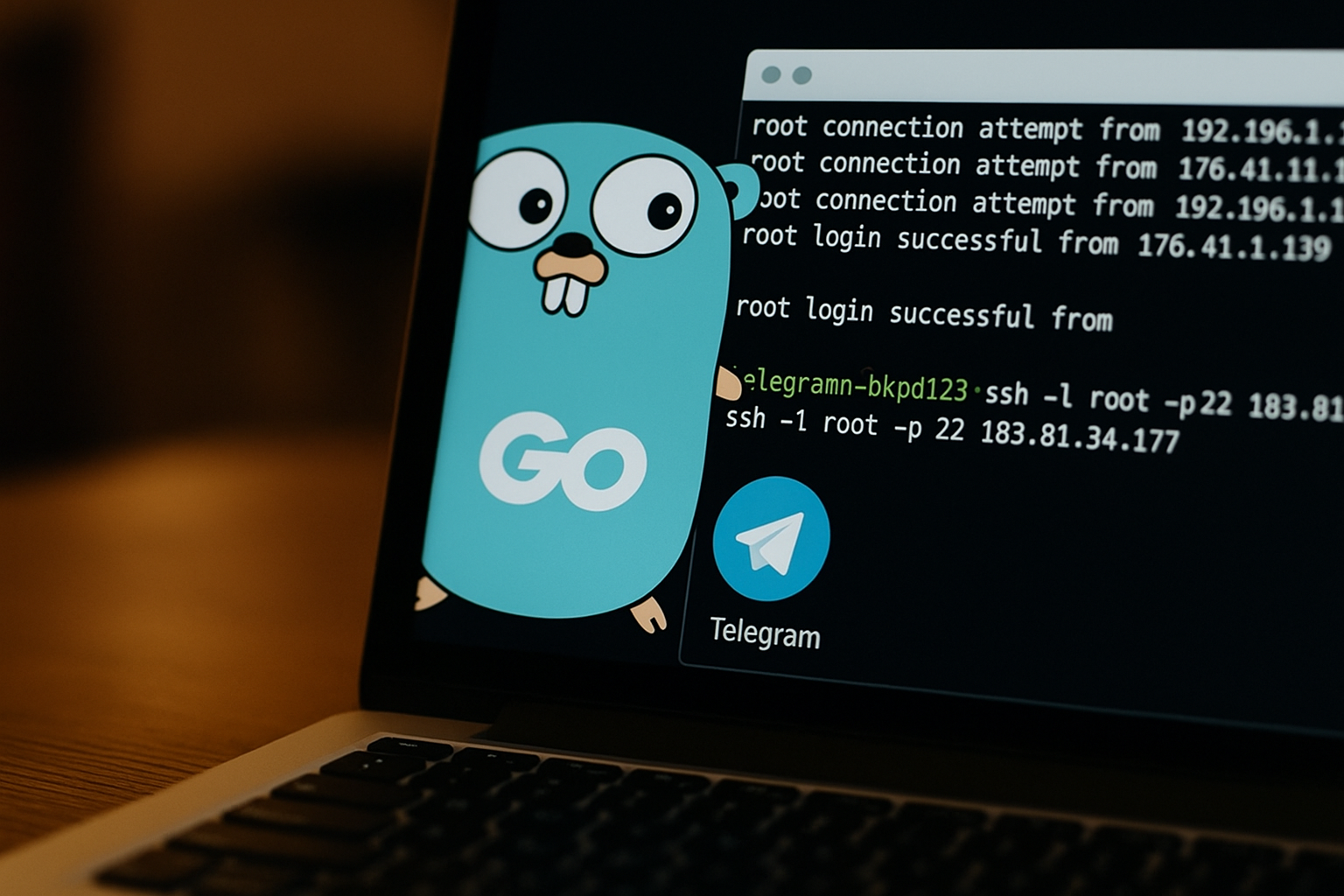
Malicious Go module masquerades as SSH brute-forcer, exfiltrates credentials via Telegram bot, researchers say
Security researchers have identified a malicious Go module masquerading as an SSH brute-force tool that quietly exfiltrates credentials to a threat actor via Telegram. The module, golang-random-ip-ssh-bruteforce, targets random SSH services, disables host key verification, and relays harvested data to a Telegram bot, highlighting ongoing software supply chain and credential theft risks.
-
Source-code leak exposes ERMAC Android banking trojan infrastructure, researchers say
The ERMAC Android banking trojan v3 source code was leaked online, exposing its backend, panel, and exfiltration infrastructure and signaling an expanded targeting scope of over 700 apps, along with notable operational security lapses that could invite further risk from other threat actors.
-
Noodlophile Infostealer Campaign Uses Legal-Threat Phishing to Target Businesses, Researchers Warn
Security researchers warn of a spear-phishing campaign leveraging legal-threat prompts to deploy the Noodlophile infostealer, using DLL side-loading in legitimate applications and malicious archives to exfiltrate cookies, payment data and system information across global targets.